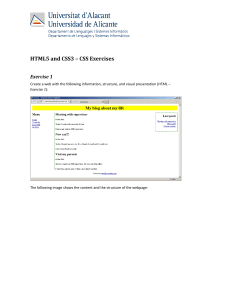
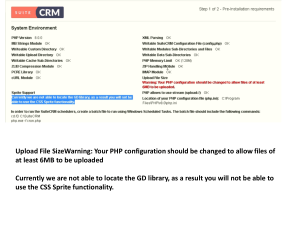
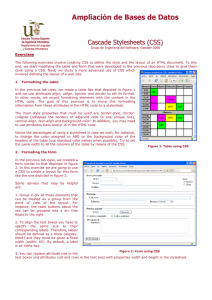
- Ninguna Categoria
Sx300 Switch & Firewall Configuration Examples
Anuncio
Sx300 Series Switches Typical Configuration Examples 2 2 Comprehensive Configuration Examples Comprehensive Configuration Examples NOTICE The solution that uses VXLAN to build virtual networks on campus networks is a large- and medium-sized campus network solution (virtualization scenario). For details about the solution, see the CloudCampus Solution. 2.1 Typical Configuration for Interoperation Between Switches and Firewalls 2.2 Typical Configuration for Interoperation Between Switches and Routers 2.3 Typical NGFW Module Configuration 2.1 Typical Configuration for Interoperation Between Switches and Firewalls 2.1.1 Example for Configuring a Layer 2 Switch to Work with a Firewall for Internet Access Layer 2 Switch Layer 2 switches perform only Layer 2 forwarding instead of Layer 3 forwarding. That is, Layer 2 switches support only Layer 2 switches instead of Layer 3 features such as routing. Layer 2 switches are typically deployed at the access layer and cannot function as gateways of users. Configuration Notes Switch configurations used in this example apply to all versions of all S series switches. This example uses firewall configurations of USG6650 V500R001C60. For other firewall configurations, see the corresponding documentation. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 4 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Networking Requirements In Figure 2-1, a company has multiple departments that belong to different network segments, and each department needs to access the Internet. It is required that users access the Internet through the Layer 2 switch and firewall and that the firewall function as the gateway of users. Figure 2-1 Configuring a Layer 2 switch to work with a firewall for Internet access Configuration Roadmap The configuration roadmap is as follows: 1. Configure interface-based VLAN assignment on the switch for Layer 2 forwarding. 2. Configure the firewall as the gateway of users to implement Layer 3 forwarding across network segments through sub-interfaces or VLANIF interfaces. 3. Configure the firewall as the DHCP server to assign IP addresses to users. 4. Configure a security interzone policy for the firewall so that packets of different zones can be forwarded. 5. Configure the PAT function on the firewall to enable intranet users to access the Internet. Procedure Step 1 Configure the switch. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 5 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples # Configure the interfaces connected to users. <Quidway> system-view [Quidway] sysname Switch [Switch] vlan batch 2 3 [Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] port link-type access //Set the link type of the interface to access. [Switch-GigabitEthernet0/0/2] port default vlan 2 //Add the interface to VLAN 2. [Switch-GigabitEthernet0/0/2] quit [Switch] interface gigabitethernet 0/0/3 [Switch-GigabitEthernet0/0/3] port link-type access [Switch-GigabitEthernet0/0/3] port default vlan 3 [Switch-GigabitEthernet0/0/3] quit # Configure the interface connected to the firewall. [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type trunk [Switch-GigabitEthernet0/0/1] port trunk allow-pass vlan 2 3 //Configure the interface as a trunk interface to transparently transmit packets from VLAN 2 and VLAN 3. [Switch-GigabitEthernet0/0/1] quit Step 2 Configure the firewall. Two methods are available to configure a firewall: one is to configure subinterfaces and the other is to configure VLANIF interfaces. ● Configure the firewall to terminate VLAN tags through sub-interfaces to implement Layer 3 forwarding across network segments. # Configure sub-interfaces for VLAN tag termination. <USG6600> system-view [USG6600] interface gigabitethernet 1/0/1.1 [USG6600-GigabitEthernet1/0/1.1] vlan-type dot1q 2 [USG6600-GigabitEthernet1/0/1.1] ip address 192.168.1.1 24 [USG6600-GigabitEthernet1/0/1.1] quit [USG6600] interface gigabitethernet 1/0/1.2 [USG6600-GigabitEthernet1/0/1.2] vlan-type dot1q 3 [USG6600-GigabitEthernet1/0/1.2] ip address 192.168.2.1 24 [USG6600-GigabitEthernet1/0/1.2] quit # Configure the DHCP function to assign IP addresses to intranet users and specify the DNS server address. [USG6600] dhcp enable [USG6600] interface gigabitethernet 1/0/1.1 [USG6600-GigabitEthernet1/0/1.1] dhcp select interface //Enable the DHCP server function on the interface and configure it to use an interface address pool. [USG6600-GigabitEthernet1/0/1.1] dhcp server dns-list 114.114.114.114 223.5.5.5 //The configured DNS-list 114.114.114.114 is a public DNS server address, which is the same for carriers. In practice, the DNS-list address needs to be configured based on the DNS assigned to a carrier.[USG6600GigabitEthernet1/0/1.1] quit [USG6600] interface gigabitethernet 1/0/1.2 [USG6600-GigabitEthernet1/0/1.2] dhcp select interface [USG6600-GigabitEthernet1/0/1.2] dhcp server dns-list 114.114.114.114 223.5.5.5 [USG6600-GigabitEthernet1/0/1.2] quit # Configure a public network interface IP address and a static route. [USG6600] interface gigabitethernet 1/0/2 [USG6600-GigabitEthernet1/0/2] ip address 200.0.0.2 255.255.255.0 //Configure an IP address 200.0.0.2 for GE0/0/2 connected to the public network. [USG6600-GigabitEthernet1/0/2] quit [USG6600] ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 //Configure a static default route with the next hop pointing to the public IP address 200.0.0.1. # Configure security zones. [USG6600] firewall zone trust //Configure a trust zone. [USG6600-zone-trust] add interface gigabitethernet 1/0/1 [USG6600-zone-trust] add interface gigabitethernet 1/0/1.1 Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 6 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [USG6600-zone-trust] add interface gigabitethernet 1/0/1.2 [USG6600-zone-trust] quit [USG6600] firewall zone untrust //Configure an untrust zone. [USG6600-zone-untrust] add interface gigabitethernet 1/0/2 [USG6600-zone-untrust] quit # Configure a security policy to allow inter-zone access. [USG6600] security-policy [USG6600-policy-security] rule name policy1 [USG6600-policy-security-rule-policy1] source-zone trust [USG6600-policy-security-rule-policy1] destination-zone untrust [USG6600-policy-security-rule-policy1] source-address 192.168.0.0 mask 255.255.0.0 [USG6600-policy-security-rule-policy1] action permit [USG6600-policy-security-rule-policy1] quit [USG6600-policy-security] quit # Configure a PAT address pool to allow interface address translation. [USG6600] nat address-group addressgroup1 [USG6600-address-group-addressgroup1] mode pat [USG6600-address-group-addressgroup1] route enable [USG6600-address-group-addressgroup1] section 0 200.0.0.2 200.0.0.2 address [USG6600-address-group-addressgroup1] quit //Translated public IP # Configure a PAT policy so that source IP addresses are automatically translated when devices on a specified network segment of an internal network access the Internet. [USG6600] nat-policy [USG6600-policy-nat] rule name policy_nat1 [USG6600-policy-nat-rule-policy_nat1] source-zone trust [USG6600-policy-nat-rule-policy_nat1] destination-zone untrust [USG6600-policy-nat-rule-policy_nat1] source-address 192.168.0.0 mask 255.255.0.0 //Source IP address that can be translated using PAT [USG6600-policy-nat-rule-policy_nat1] action nat address-group addressgroup1 [USG6600-policy-nat-rule-policy_nat1] quit [USG6600-policy-nat] quit [USG6600] quit ● Configure VLANIF interfaces on the firewall to implement Layer 3 forwarding across network segments. # Configure VLANIF interfaces. <USG6600> system-view [USG6600] vlan batch 2 3 [USG6600] interface gigabitethernet 1/0/1 [USG6600-GigabitEthernet1/0/1] portswitch //Change the Ethernet interface from Layer 3 mode to Layer 2 mode. If it has worked in Layer 2 mode, skip this step. [USG6600-GigabitEthernet1/0/1] port link-type hybrid [USG6600-GigabitEthernet1/0/1] port hybrid tagged vlan 2 to 3 [USG6600-GigabitEthernet1/0/1] quit [USG6600] interface vlanif 2 [USG6600-Vlanif2] ip address 192.168.1.1 24 //Configure the IP address of VLANIF2 as the gateway address of PC1. [USG6600-Vlanif2] quit [USG6600] interface vlanif 3 [USG6600-Vlanif3] ip address 192.168.2.1 24 //Configure the IP address of VLANIF3 as the gateway address of PC2. [USG6600-Vlanif3] quit # Configure the DHCP and DNS functions. [USG6600] dhcp enable [USG6600] interface vlanif 2 [USG6600-Vlanif2] dhcp select interface [USG6600-Vlanif2] dhcp server dns-list 114.114.114.114 223.5.5.5 //The configured DNS-list 114.114.114.114 is a public DNS server address, which is the same for carriers. In practice, the DNSlist address needs to be configured based on the DNS assigned to a carrier.[USG6600-Vlanif2] quit [USG6600] interface vlanif 3 [USG6600-Vlanif3] dhcp select interface [USG6600-Vlanif3] dhcp server dns-list 114.114.114.114 223.5.5.5 [USG6600-Vlanif3] quit Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 7 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples # Configure a public network interface IP address and a static route. [USG6600] interface gigabitethernet 1/0/2 [USG6600-GigabitEthernet1/0/2] ip address 200.0.0.2 255.255.255.0 [USG6600-GigabitEthernet1/0/2] quit [USG6600] ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 //Configure a static default route with the next hop pointing to the public IP address 200.0.0.1. # Configure security zones. [USG6600] firewall zone trust [USG6600-zone-trust] add interface gigabitethernet 1/0/1 [USG6600-zone-trust] add interface vlanif 2 [USG6600-zone-trust] add interface vlanif 3 [USG6600-zone-trust] quit [USG6600] firewall zone untrust [USG6600-zone-untrust] add interface gigabitethernet 1/0/2 [USG6600-zone-untrust] quit # Configure a security policy to allow inter-zone access. [USG6600] security-policy [USG6600-policy-security] rule name policy1 [USG6600-policy-security-rule-policy1] source-zone trust [USG6600-policy-security-rule-policy1] destination-zone untrust [USG6600-policy-security-rule-policy1] source-address 192.168.0.0 mask 255.255.0.0 [USG6600-policy-security-rule-policy1] action permit [USG6600-policy-security-rule-policy1] quit [USG6600-policy-security] quit # Configure a PAT address pool to allow interface address translation. [USG6600] nat address-group addressgroup1 [USG6600-address-group-addressgroup1] mode pat [USG6600-address-group-addressgroup1] route enable [USG6600-address-group-addressgroup1] section 0 200.0.0.2 200.0.0.2 address [USG6600-address-group-addressgroup1] quit //Translated public IP # Configure a PAT policy so that source IP addresses are automatically translated when devices on a specified network segment of an internal network access the Internet. [USG6600] nat-policy [USG6600-policy-nat] rule name policy_nat1 [USG6600-policy-nat-rule-policy_nat1] source-zone trust [USG6600-policy-nat-rule-policy_nat1] destination-zone untrust [USG6600-policy-nat-rule-policy_nat1] source-address 192.168.0.0 mask 255.255.0.0 //Source IP address that can be translated using PAT [USG6600-policy-nat-rule-policy_nat1] action nat address-group addressgroup1 [USG6600-policy-nat-rule-policy_nat1] quit [USG6600-policy-nat] quit [USG6600] quit Step 3 Check the configuration. Configure an IP address 192.168.1.2/24 and a gateway address 192.168.1.1 for PC1, and configure an IP address 192.168.2.2/24 and a gateway address 192.168.2.1 for PC2. Configure an IP address 200.0.0.1/24 and a gateway address 200.0.0.2 for external network. After the configurations are complete, PC1 and PC2 can ping the external network IP address 200.0.0.1/24 and access the Internet. ----End Configuration Files ● Issue 34 (2022-10-26) Switch configuration file Copyright © Huawei Technologies Co., Ltd. 8 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples # sysname Switch # vlan batch 2 to 3 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 2 to 3 # interface GigabitEthernet0/0/2 port link-type access port default vlan 2 # interface GigabitEthernet0/0/3 port link-type access port default vlan 3 # return ● USG configuration file (used when the firewall performs Layer 3 forwarding through sub-interfaces) # interface GigabitEthernet1/0/1 # interface GigabitEthernet1/0/1.1 vlan-type dot1q 2 ip address 192.168.1.1 255.255.255.0 dhcp select interface dhcp server dns-list 114.114.114.114 223.5.5.5 # interface GigabitEthernet1/0/1.2 vlan-type dot1q 3 ip address 192.168.2.1 255.255.255.0 dhcp select interface dhcp server dns-list 114.114.114.114 223.5.5.5 # interface GigabitEthernet1/0/2 ip address 200.0.0.2 255.255.255.0 # firewall zone trust set priority 85 add interface GigabitEthernet1/0/1 add interface GigabitEthernet1/0/1.1 add interface GigabitEthernet1/0/1.2 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/2 # ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 # nat address-group addressgroup1 0 mode pat route enable section 0 200.0.0.2 200.0.0.2 # security-policy rule name policy1 source-zone trust destination-zone untrust source-address 192.168.0.0 mask 255.255.0.0 action permit # nat-policy rule name policy_nat1 source-zone trust destination-zone untrust source-address 192.168.0.0 mask 255.255.0.0 action nat address-group addressgroup1 Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 9 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples # return ● USG configuration file (used when the firewall performs Layer 3 forwarding through VLANIF interfaces) # vlan batch 2 to 3 # interface Vlanif2 ip address 192.168.1.1 255.255.255.0 dhcp server dns-list 114.114.114.114 223.5.5.5 # interface Vlanif3 ip address 192.168.2.1 255.255.255.0 dhcp select interface dhcp server dns-list 114.114.114.114 223.5.5.5 # interface GigabitEthernet1/0/1 portswitch port hybrid tagged vlan 2 to 3 # interface GigabitEthernet1/0/2 ip address 200.0.0.2 255.255.255.0 # firewall zone trust set priority 85 add interface GigabitEthernet1/0/1 add interface Vlanif2 add interface Vlanif3 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/2 # ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 # nat address-group addressgroup1 0 mode pat route enable section 0 200.0.0.2 200.0.0.2 # security-policy rule name policy1 source-zone trust destination-zone untrust source-address 192.168.0.0 mask 255.255.0.0 action permit # nat-policy rule name policy_nat1 source-zone trust destination-zone untrust source-address 192.168.0.0 mask 255.255.0.0 action nat address-group addressgroup1 # return 2.1.2 Example for Configuring a Layer 3 Switch to Work with a Firewall for Internet Access Layer 3 Switch Layer 3 switches provide the routing function, which indicates a network-layer function in the OSI model. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 10 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Layer 3 switches can work at Layer 2 and Layer 3 and be deployed at the access layer or aggregation layer as user gateways. Configuration Notes ● This example uses firewall configurations of USG6650 V500R001C60. For other firewall configurations, see the corresponding documentation. ● This example applies to the following products and versions when a switch functions as a DHCP server: ● – V200R005C00SPC300 and later versions: S2350-EI, S5300-LI – S2320-EI, S3300-SI, S3300-EI, S3300-HI – S5300-SI, S5300-EI, S5300-HI, S5310-EI, S5320-LI, S5320-SI, S5320-EI, S5320-HI, S5330-SI, S5330-HI, S5331-S, S5331-H, S5332-H, S5335-L, S5335-L1, S5335-S, S5336-S – S6300-EI, S6320-SI, S6320-EI, S6320-HI, S6330-H – S9303, S9306, S9312, S9310, S9310X, S9300X-4, S9300X-8, S9300X-12, S9303E, S9306E, S9312E For the product models whose applicable versions are not listed above, see Table 1-1 in "Applicable Products and Versions" for details. Networking Requirements In Figure 2-2, a company has multiple departments that belong to different network segments, and each department needs to access the Internet. It is required that users access the Internet through the Layer 3 switch and firewall and that the Layer 3 switch function as the gateway of users. Figure 2-2 Configuring a Layer 3 switch to work with a firewall for Internet access Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 11 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Configuration Roadmap The configuration roadmap is as follows: 1. Configure the switch as the gateway of users to allow users to communicate across network segments through VLANIF interfaces. 2. Configure the switch as the DHCP server to assign IP addresses to users. 3. Configure an interzone security policy for the firewall so that packets of different zones can be forwarded. 4. Configure the PAT function on the firewall to enable intranet users to access the Internet. Procedure Step 1 Configure the switch. # Configure the interfaces connected to users and corresponding VLANIF interfaces. <Quidway> system-view [Quidway] sysname Switch [Switch] vlan batch 2 3 [Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] port link-type access //Set the link type of the interface to access. [Switch-GigabitEthernet0/0/2] port default vlan 2 //Add the interface to VLAN 2. [Switch-GigabitEthernet0/0/2] quit [Switch] interface gigabitethernet 0/0/3 [Switch-GigabitEthernet0/0/3] port link-type access [Switch-GigabitEthernet0/0/3] port default vlan 3 [Switch-GigabitEthernet0/0/3] quit [Switch] interface vlanif 2 [Switch-Vlanif2] ip address 192.168.1.1 24 [Switch-Vlanif2] quit [Switch] interface vlanif 3 [Switch-Vlanif3] ip address 192.168.2.1 24 [Switch-Vlanif3] quit # Configure the interface connected to the firewall and corresponding VLANIF interface. [Switch] vlan batch 100 [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type access [Switch-GigabitEthernet0/0/1] port default vlan 100 [Switch-GigabitEthernet0/0/1] quit [Switch] interface vlanif 100 [Switch-Vlanif100] ip address 192.168.100.2 24 [Switch-Vlanif100] quit # Configure the default route. [Switch] ip route-static 0.0.0.0 0.0.0.0 192.168.100.1 //The next hop of the default route is the IP address 192.168.100.1 of the firewall interface. # Configure the DHCP server. [Switch] dhcp enable [Switch] interface vlanif 2 [Switch-Vlanif2] dhcp select interface //DHCP uses an interface address pool to assign IP addresses to intranet users. [Switch-Vlanif2] dhcp server dns-list 114.114.114.114 223.5.5.5 //The configured DNS-list 114.114.114.114 is a public DNS server address, which is the same for carriers. In practice, the DNS-list address needs to be configured based on the DNS assigned to a carrier. [Switch-Vlanif2] quit Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 12 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [Switch] interface vlanif 3 [Switch-Vlanif3] dhcp select interface [Switch-Vlanif3] dhcp server dns-list 114.114.114.114 223.5.5.5 [Switch-Vlanif3] quit Step 2 Configure the firewall. # Configure an IP address for the interface connected to the switch. <USG> system-view [USG] interface gigabitethernet 1/0/1 [USG-GigabitEthernet1/0/1] ip address 192.168.100.1 255.255.255.0 [USG-GigabitEthernet1/0/1] quit # Configure an IP address for the interface connected to the Internet. [USG] interface gigabitethernet 1/0/2 [USG-GigabitEthernet1/0/2] ip address 200.0.0.2 255.255.255.0 //The IP address of the interface connected to the Internet is on the same network segment as the public IP address. [USG-GigabitEthernet1/0/2] quit # Configure a default route and a return route. [USG] ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 //Configure a static default route with the next hop pointing to the public IP address 200.0.0.1. [USG] ip route-static 192.168.0.0 255.255.0.0 192.168.100.2 //Configure a return route with the next hop pointing to the IP address 192.168.100.2 of the switch's uplink interface. # Configure security zones. [USG] firewall zone trust //Configure a trust zone. [USG-zone-trust] add interface gigabitethernet 1/0/1 [USG-zone-trust] quit [USG] firewall zone untrust //Configure an untrust zone. [USG-zone-untrust] add interface gigabitethernet 1/0/2 [USG-zone-untrust] quit # Configure a security policy to allow inter-zone access. [USG6600] security-policy [USG6600-policy-security] rule name policy1 [USG6600-policy-security-rule-policy1] source-zone trust [USG6600-policy-security-rule-policy1] destination-zone untrust [USG6600-policy-security-rule-policy1] source-address 192.168.0.0 mask 255.255.0.0 [USG6600-policy-security-rule-policy1] action permit [USG6600-policy-security-rule-policy1] quit [USG6600-policy-security] quit # Configure a PAT address pool to allow interface address translation. [USG6600] nat address-group addressgroup1 [USG6600-address-group-addressgroup1] mode pat [USG6600-address-group-addressgroup1] route enable [USG6600-address-group-addressgroup1] section 0 200.0.0.2 200.0.0.2 [USG6600-address-group-addressgroup1] quit //Translated public IP address # Configure a PAT policy so that source IP addresses are automatically translated when devices on a specified network segment of an internal network access the Internet. [USG6600] nat-policy [USG6600-policy-nat] rule name policy_nat1 [USG6600-policy-nat-rule-policy_nat1] source-zone trust [USG6600-policy-nat-rule-policy_nat1] destination-zone untrust [USG6600-policy-nat-rule-policy_nat1] source-address 192.168.0.0 mask 255.255.0.0 //Source IP address that can be translated using PAT [USG6600-policy-nat-rule-policy_nat1] action nat address-group addressgroup1 [USG6600-policy-nat-rule-policy_nat1] quit [USG6600-policy-nat] quit [USG6600] quit Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 13 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Step 3 Check the configuration. Configure an IP address 192.168.1.2/24 and a gateway address 192.168.1.1 for PC1, and configure an IP address 192.168.2.2/24 and a gateway address 192.168.2.1 for PC2. Configure an IP address 200.0.0.1/24 and a gateway address 200.0.0.2 for external network. After the configurations are complete, PC1 and PC2 can ping the external network IP address 200.0.0.1/24 and access the Internet. ----End Configuration Files ● ● Issue 34 (2022-10-26) Switch configuration file # sysname Switch # vlan batch 2 to 3 100 # dhcp enable # interface Vlanif2 ip address 192.168.1.1 255.255.255.0 dhcp select interface dhcp server dns-list 114.114.114.114 223.5.5.5 # interface Vlanif3 ip address 192.168.2.1 255.255.255.0 dhcp select interface dhcp server dns-list 114.114.114.114 223.5.5.5 # interface Vlanif100 ip address 192.168.100.2 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type access port default vlan 100 # interface GigabitEthernet0/0/2 port link-type access port default vlan 2 # interface GigabitEthernet0/0/3 port link-type access port default vlan 3 # ip route-static 0.0.0.0 0.0.0.0 192.168.100.1 # return USG configuration file # interface GigabitEthernet1/0/1 ip address 192.168.100.1 255.255.255.0 # interface GigabitEthernet0/0/2 ip address 200.0.0.2 255.255.255.0 # firewall zone trust set priority 85 add interface GigabitEthernet1/0/1 # firewall zone untrust set priority 5 Copyright © Huawei Technologies Co., Ltd. 14 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples add interface GigabitEthernet0/0/2 # ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 ip route-static 192.168.0.0 255.255.0.0 192.168.100.2 # nat address-group addressgroup1 0 mode pat route enable section 0 200.0.0.2 200.0.0.2 # security-policy rule name policy1 source-zone trust destination-zone untrust source-address 192.168.0.0 mask 255.255.0.0 action permit # nat-policy rule name policy_nat1 source-zone trust destination-zone untrust source-address 192.168.0.0 mask 255.255.0.0 action nat address-group addressgroup1 # return 2.2 Typical Configuration for Interoperation Between Switches and Routers 2.2.1 Example for Configuring a Layer 2 Switch to Work with a Router for Internet Access Layer 2 Switch Layer 2 switches perform only Layer 2 forwarding instead of Layer 3 forwarding. That is, Layer 2 switches support only Layer 2 switches instead of Layer 3 features such as routing. Layer 2 switches are typically deployed at the access layer and cannot function as gateways of users. Configuration Notes Switch configurations used in this example apply to all versions of all S series switches. This example uses router configurations of AR3600 V200R007C00SPCc00. For other router configurations, see the corresponding documentation. Networking Requirements In Figure 2-3, a company has multiple departments that belong to different network segments, and each department needs to access the Internet. It is required that users access the Internet through the Layer 2 switch and router and that the router function as the gateway of users. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 15 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Figure 2-3 Configuring a Layer 2 switch to work with a router for Internet access Configuration Roadmap The configuration roadmap is as follows: 1. Configure interface-based VLAN assignment on the switch for Layer 2 forwarding. 2. Configure the router as the gateway of users to implement Layer 3 forwarding across network segments through sub-interfaces or VLANIF interfaces. 3. Configure the router as the DHCP server to assign IP addresses to users. 4. Configure the NAT function on the router to enable intranet users to access the Internet. Procedure Step 1 Configure the switch. # Configure the interfaces connected to users. <Quidway> system-view [Quidway] sysname Switch [Switch] vlan batch 2 3 [Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] port link-type access //Set the link type of the interface to access. [Switch-GigabitEthernet0/0/2] port default vlan 2 //Add the interface to VLAN 2. [Switch-GigabitEthernet0/0/2] quit [Switch] interface gigabitethernet 0/0/3 [Switch-GigabitEthernet0/0/3] port link-type access Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 16 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [Switch-GigabitEthernet0/0/3] port default vlan 3 [Switch-GigabitEthernet0/0/3] quit # Configure the interface connected to the router. [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type trunk [Switch-GigabitEthernet0/0/1] port trunk allow-pass vlan 2 3 //Configure the interface as a trunk interface to transparently transmit packets from VLAN 2 and VLAN 3. [Switch-GigabitEthernet0/0/1] quit Step 2 Configure the router. Two methods are available to configure a router: one is to configure subinterfaces and the other is to configure VLANIF interfaces. ● Configure the router to terminate VLAN tags through sub-interfaces to implement Layer 3 forwarding across network segments. # Configure sub-interfaces for VLAN tag termination. <Huawei> system-view [Huawei] sysname Router [Router] vlan batch 2 3 [Router] interface gigabitethernet 0/0/1.1 [Router-GigabitEthernet0/0/1.1] dot1q termination vid 2 [Router-GigabitEthernet0/0/1.1] ip address 192.168.1.1 24 [Router-GigabitEthernet0/0/1.1] arp broadcast enable //By default, ARP broadcast on a VLAN tag termination sub-interface is disabled on AR routers in a version earlier than V200R003C01 and enabled in V200R003C01 and later versions. [Router-GigabitEthernet0/0/1.1] quit [Router] interface gigabitethernet 0/0/1.2 [Router-GigabitEthernet0/0/1.2] dot1q termination vid 3 [Router-GigabitEthernet0/0/1.2] ip address 192.168.2.1 24 [Router-GigabitEthernet0/0/1.2] arp broadcast enable [Router-GigabitEthernet0/0/1.2] quit # Configure the DHCP function to assign IP addresses to intranet users and specify the DNS server address. [Router] dhcp enable [Router] interface gigabitethernet 0/0/1.1 [Router-GigabitEthernet0/0/1.1] dhcp select interface //DHCP uses an interface address pool to assign IP addresses to intranet users. [Router-GigabitEthernet0/0/1.1] dhcp server dns-list 114.114.114.114 223.5.5.5 //The configured DNS-list 114.114.114.114 is a public DNS server address, which is the same for carriers. In practice, the DNS-list address needs to be configured based on the DNS assigned to a carrier. [Router-GigabitEthernet0/0/1.1] quit [Router] interface gigabitethernet 0/0/1.2 [Router-GigabitEthernet0/0/1.2] dhcp select interface [Router-GigabitEthernet0/0/1.2] dhcp server dns-list 114.114.114.114 223.5.5.5 [Router-GigabitEthernet0/0/1.2] quit # Configure a public network interface IP address and a static route. [Router] interface gigabitethernet 0/0/2 [Router-GigabitEthernet0/0/2] ip address 200.0.0.2 255.255.255.0 //Configure an IP address 200.0.0.2 for GE0/0/2 connected to the public network. [Router-GigabitEthernet0/0/2] quit [Router] ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 //Configure a static default route with the next hop pointing to the public IP address 200.0.0.1. # Configure the NAT function to enable intranet users to access the Internet. [Router] acl number 2001 [Router-acl-basic-2001] rule 5 permit source 192.168.0.0 0.0.255.255 //NAT takes effect only for source IP addresses on the network segment 192.168.0.0/16 and translates only source IP addresses of outgoing packets on GE0/0/2. [Router-acl-basic-2001] quit [Router] interface gigabitethernet 0/0/2 [Router-GigabitEthernet0/0/2] nat outbound 2001 [Router-GigabitEthernet0/0/2] quit Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 17 Sx300 Series Switches Typical Configuration Examples ● 2 Comprehensive Configuration Examples Configure VLANIF interfaces on the router to implement Layer 3 forwarding across network segments. # Configure VLANIF interfaces. <Huawei> system-view [Huawei] sysname Router [Router] vlan batch 2 3 [Router] interface gigabitethernet 0/0/1 [Router-GigabitEthernet0/0/1] portswitch //Change the Ethernet interface from Layer 3 mode to Layer 2 mode. If it has worked in Layer 2 mode, skip this step. [Router-GigabitEthernet0/0/1] port link-type trunk [Router-GigabitEthernet0/0/1] port trunk allow-pass vlan 2 3 [Router-GigabitEthernet0/0/1] quit [Router] interface vlanif 2 [Router-vlanif2] ip address 192.168.1.1 24 //Configure the IP address of VLANIF2 as the gateway address of PC1. [Router-vlanif2] quit [Router] interface vlanif 3 [Router-vlanif3] ip address 192.168.2.1 24 //Configure the IP address of VLANIF3 as the gateway address of PC2. [Router-vlanif3] quit # Configure the DHCP function to assign IP addresses to intranet users and specify the DNS server address. [Router] dhcp enable [Router] interface vlanif 2 [Router-Vlanif2] dhcp select interface [Router-Vlanif2] dhcp server dns-list 114.114.114.114 223.5.5.5 //The configured DNS-list 114.114.114.114 is a public DNS server address, which is the same for carriers. In practice, the DNSlist address needs to be configured based on the DNS assigned to a carrier. [Router-Vlanif2] quit [Router] interface vlanif 3 [Router-Vlanif3] dhcp select interface [Router-Vlanif3] dhcp server dns-list 114.114.114.114 223.5.5.5 [Router-Vlanif3] quit # Configure a public network interface IP address and a static route. [Router] interface gigabitethernet 0/0/2 [Router-GigabitEthernet0/0/2] ip address 200.0.0.2 255.255.255.0 [Router-GigabitEthernet0/0/2] quit [Router] ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 //Configure a static default route with the next hop pointing to the public IP address 200.0.0.1. # Configure the NAT function to enable intranet users to access the Internet. [Router] acl number 2001 [Router-acl-basic-2001] rule 5 permit source 192.168.0.0 0.0.255.255 //NAT takes effect only for source IP addresses on the network segment 192.168.0.0/16 and translates only source IP addresses of outgoing packets on GE0/0/2. [Router-acl-basic-2001] quit [Router] interface gigabitethernet 0/0/2 [Router-GigabitEthernet0/0/2] nat outbound 2001 [Router-GigabitEthernet0/0/2] quit Step 3 Check the configuration. Configure an IP address 192.168.1.2/24 and a gateway address 192.168.1.1 for PC1, and configure an IP address 192.168.2.2/24 and a gateway address 192.168.2.1 for PC2. Configure an IP address 200.0.0.1/24 and a gateway address 200.0.0.2 for external network. After the configurations are complete, PC1 and PC2 can ping the external network IP address 200.0.0.1/24 and access the Internet. ----End Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 18 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Configuration Files ● Switch configuration file # sysname Switch # vlan batch 2 to 3 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 2 to 3 # interface GigabitEthernet0/0/2 port link-type access port default vlan 2 # interface GigabitEthernet0/0/3 port link-type access port default vlan 3 # return ● Router configuration file (used when the router performs Layer 3 forwarding through sub-interfaces) # sysname Router # vlan batch 2 to 3 # dhcp enable # acl number 2001 rule 5 permit source 192.168.0.0 0.0.255.255 # interface GigabitEthernet0/0/1 # interface GigabitEthernet0/0/1.1 dot1q termination vid 2 ip address 192.168.1.1 255.255.255.0 arp broadcast enable dhcp select interface dhcp server dns-list 114.114.114.114 223.5.5.5 # interface GigabitEthernet0/0/1.2 dot1q termination vid 3 ip address 192.168.2.1 255.255.255.0 arp broadcast enable dhcp select interface dhcp server dns-list 114.114.114.114 223.5.5.5 # interface GigabitEthernet0/0/2 ip address 200.0.0.2 255.255.255.0 nat outbound 2001 # ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 # return ● Router configuration file (used when the router performs Layer 3 forwarding through VLANIF interfaces) # sysname Router # vlan batch 2 to 3 # dhcp enable # acl number 2001 rule 5 permit source 192.168.0.0 0.0.255.255 Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 19 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples # interface Vlanif2 ip address 192.168.1.1 255.255.255.0 dhcp select interface dhcp server dns-list 114.114.114.114 223.5.5.5 # interface Vlanif3 ip address 192.168.2.1 255.255.255.0 dhcp select interface dhcp server dns-list 114.114.114.114 223.5.5.5 # interface GigabitEthernet0/0/1 portswitch port link-type trunk port trunk allow-pass vlan 2 to 3 # interface GigabitEthernet0/0/2 ip address 200.0.0.2 255.255.255.0 nat outbound 2001 # ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 # return 2.2.2 Example for Configuring a Layer 3 Switch to Work with a Router for Internet Access Layer 3 Switch Layer 3 switches provide the routing function, which indicates a network-layer function in the OSI model. Layer 3 switches can work at Layer 2 and Layer 3 and be deployed at the access layer or aggregation layer as user gateways. Configuration Notes ● This example uses router configurations of AR3600 V200R007C00SPCc00. For other router configurations, see the corresponding documentation. ● This example applies to the following products and versions when a switch functions as a DHCP server: ● – V200R005C00SPC300 and later versions: S2350-EI, S5300-LI – S2320-EI, S3300-SI, S3300-EI, S3300-HI – S5300-SI, S5300-EI, S5300-HI, S5310-EI, S5320-LI, S5320-SI, S5320-EI, S5320-HI, S5330-SI, S5330-HI, S5331-S, S5331-H, S5332-H, S5335-L, S5335-L1, S5335-S, S5336-S – S6300-EI, S6320-SI, S6320-EI, S6320-HI, S6330-H – S9303, S9306, S9312, S9310, S9310X, S9300X-4, S9300X-8, S9300X-12, S9303E, S9306E, S9312E For the product models whose applicable versions are not listed above, see Table 1-1 in "Applicable Products and Versions" for details. Networking Requirements In Figure 2-4, a company has multiple departments that belong to different network segments, and each department needs to access the Internet. It is Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 20 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples required that users access the Internet through the Layer 3 switch and router and that the Layer 3 switch function as the gateway of users. Figure 2-4 Configuring a Layer 3 switch to work with a router for Internet access Configuration Roadmap The configuration roadmap is as follows: 1. Configure the switch as the gateway of users to allow users to communicate across network segments through VLANIF interfaces. 2. Configure the switch as the DHCP server to assign IP addresses to users. 3. Configure the NAT function on the router to enable intranet users to access the Internet. Procedure Step 1 Configure the switch. # Configure the interfaces connected to users and corresponding VLANIF interfaces. <Quidway> system-view [Quidway] sysname Switch [Switch] vlan batch 2 3 [Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] port link-type access //Set the link type of the interface to access. [Switch-GigabitEthernet0/0/2] port default vlan 2 //Add the interface to VLAN 2. [Switch-GigabitEthernet0/0/2] quit [Switch] interface gigabitethernet 0/0/3 [Switch-GigabitEthernet0/0/3] port link-type access Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 21 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [Switch-GigabitEthernet0/0/3] port default vlan 3 [Switch-GigabitEthernet0/0/3] quit [Switch] interface vlanif 2 [Switch-Vlanif2] ip address 192.168.1.1 24 [Switch-Vlanif2] quit [Switch] interface vlanif 3 [Switch-Vlanif3] ip address 192.168.2.1 24 [Switch-Vlanif3] quit # Configure the interface connected to the router and corresponding VLANIF interface. [Switch] vlan batch 100 [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type access [Switch-GigabitEthernet0/0/1] port default vlan 100 [Switch-GigabitEthernet0/0/1] quit [Switch] interface vlanif 100 [Switch-Vlanif100] ip address 192.168.100.2 24 [Switch-Vlanif100] quit # Configure the default route. [Switch] ip route-static 0.0.0.0 0.0.0.0 192.168.100.1 //The next hop of the default route is the IP address 192.168.100.1 of the router interface. # Configure the DHCP server. [Switch] dhcp enable [Switch] interface vlanif 2 [Switch-Vlanif2] dhcp select interface //DHCP uses an interface address pool to assign IP addresses to intranet users. [Switch-Vlanif2] dhcp server dns-list 114.114.114.114 223.5.5.5 //The configured DNS-list 114.114.114.114 is a public DNS server address, which is the same for carriers. In practice, the DNS-list address needs to be configured based on the DNS assigned to a carrier. [Switch-Vlanif2] quit [Switch] interface vlanif 3 [Switch-Vlanif3] dhcp select interface [Switch-Vlanif3] dhcp server dns-list 114.114.114.114 223.5.5.5 [Switch-Vlanif3] quit Step 2 Configure the router. # Configure an IP address for the interface connected to the switch. <Huawei> system-view [Huawei] sysname Router [Router] interface gigabitethernet 0/0/1 [Router-GigabitEthernet0/0/1] ip address 192.168.100.1 255.255.255.0 //Configure the IP address 192.168.100.1 as the next-hop IP address of the switch's default route. [Router-GigabitEthernet0/0/1] quit # Configure an IP address for the interface connected to the Internet. [Router] interface gigabitethernet 0/0/2 [Router-GigabitEthernet0/0/2] ip address 200.0.0.2 255.255.255.0 //The IP address of the interface connected to the Internet is on the same network segment as the public IP address. [Router-GigabitEthernet0/0/2] quit # Configure a default route and a return route. [Router] ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 //Configure a static default route with the next hop pointing to the public IP address 200.0.0.1. [Router] ip route-static 192.168.0.0 255.255.0.0 192.168.100.2 //Configure a return route with the next hop pointing to the IP address 192.168.100.2 of the switch's uplink interface. # Configure the NAT function to enable intranet users to access the Internet. [Router] acl number 2001 [Router-acl-basic-2001] rule 5 permit source 192.168.0.0 0.0.255.255 //NAT takes effect only for source Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 22 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples IP addresses on the network segment 192.168.0.0/16 and translates only source IP addresses of outgoing packets on GE0/0/2. [Router-acl-basic-2001] quit [Router] interface gigabitethernet 0/0/2 [Router-GigabitEthernet0/0/2] nat outbound 2001 [Router-GigabitEthernet0/0/2] quit Step 3 Check the configuration. Configure an IP address 192.168.1.2/24 and a gateway address 192.168.1.1 for PC1, and configure an IP address 192.168.2.2/24 and a gateway address 192.168.2.1 for PC2. Configure an IP address 200.0.0.1/24 and a gateway address 200.0.0.2 for external network. After the configurations are complete, PC1 and PC2 can ping the external network IP address 200.0.0.1/24 and access the Internet. ----End Configuration Files ● ● Issue 34 (2022-10-26) Switch configuration file # sysname Switch # vlan batch 2 to 3 100 # dhcp enable # interface Vlanif2 ip address 192.168.1.1 255.255.255.0 dhcp select interface dhcp server dns-list 114.114.114.114 223.5.5.5 # interface Vlanif3 ip address 192.168.2.1 255.255.255.0 dhcp select interface dhcp server dns-list 114.114.114.114 223.5.5.5 # interface Vlanif100 ip address 192.168.100.2 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type access port default vlan 100 # interface GigabitEthernet0/0/2 port link-type access port default vlan 2 # interface GigabitEthernet0/0/3 port link-type access port default vlan 3 # ip route-static 0.0.0.0 0.0.0.0 192.168.100.1 # return Router configuration file # sysname Router # acl number 2001 rule 5 permit source 192.168.0.0 0.0.255.255 # Copyright © Huawei Technologies Co., Ltd. 23 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples interface GigabitEthernet0/0/1 ip address 192.168.100.1 255.255.255.0 # interface GigabitEthernet0/0/2 ip address 200.0.0.2 255.255.255.0 nat outbound 2001 # ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 ip route-static 192.168.0.0 255.255.0.0 192.168.100.2 # return 2.3 Typical NGFW Module Configuration NGFW modules are service cards used on switches. An NGFW module connects to a switch through two 20GE Ethernet links. On the two Ethernet links, the ports on one end are located on the switch, and the ports on the other end are located on the NGFW module. Services need to be configured on both the switch-side and NGFW module-side, otherwise, the NGFW module cannot work normally. The minimum NGFW module card version matching the switch is V100R001C10. These NGFW module cards are supported on the switch running V200R005C00 or later. 2.3.1 Layer 2 Load-Balancing Hot Standby on the NGFW Modules Installed on a Cluster Switch Where Redirectionbased Traffic Diversion Is Implemented Service Requirements As shown in Figure 2-5, two switches form a CSS, and two NGFW Modules are installed in slot 1 of the switches respective and implement hot standby. The NGFW Modules work at Layer 2 and are transparently connected to the network. The NGFW Modules implement security check on traffic sent by intranet users to the Internet. The traffic exchanged between different VLANs does not pass the NGFW modules. Instead, the traffic is directly forwarded by the switches. This example uses NGFW modules running V100R001C30 and switches running V200R008C00. For the configuration examples of NGFW Modules running other versions, see Deployment Guide. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 24 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Figure 2-5 Networking for Layer-2 dual-NGFW Module deployment and switch CSS NOTE The NGFW Module has two fixed internal Ethernet interfaces: GE1/0/0 to GE1/0/1. The numbering of internal Ethernet interfaces on the switch is determined by the slot in which the NGFW Module is installed. For example, when the NGFW Module is installed in slot 1 on the switch, the internal Ethernet interfaces used by the switch are XGE1/1/0/0 to XGE1/1/0/1. Eth-Trunk2 and Eth-Trunk3 are interfaces of the switches in the CSS. Deployment Solution The four interfaces connecting the switches to the NGFW modules are bundled into an Eth-Trunk interface, and traffic is distributed among the two NGFW Modules. The two NGFW Modules implement hot standby in Layer-2 load balancing mode. 1. Add the four interfaces on the switches to Eth-Trunk 10 and four interfaces on the NGFW Modules to Eth-Trunk 1. 2. Redirection is configured on the switches to direct traffic exchanged between intranet users and the Internet to the NGFW Modules. Eth-Trunk 1 is configured as an interface pair (packets entering the interface are forwarded out of the same interface after being processed) on the NGFW Modules to send traffic back to the switches. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 25 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples NOTE When the NGFW Module works in interface pair mode, the switch cannot have the loopdetection function enabled. If the switch has the loop-detection function enabled, broadcast packets are sent out at the interface. Because the NGFW Module works in interface pair mode, all packets received by the interface are sent out from this interface. This causes the switch to detect traffic loops and disable the interface. 3. The NGFW Modules implement hot standby in Layer-2 load balancing mode. Therefore, configure the VLANs to be tracked of the upstream and downstream interfaces. Figure 2-6 provides logical networking for easy understanding. Figure 2-6 Configuring hot standby on the NGFW Modules NOTE Figure 2-6 provides information only interfaces related to the switches and NGFW Modules. 4. Issue 34 (2022-10-26) Bundle GE0/0/1 and GE0/0/2 interfaces on the panel of each NGFW Module into an Eth-Trunk0 interface, which functions as the heartbeat interface and backup channel and enable hot standby. Copyright © Huawei Technologies Co., Ltd. 26 Sx300 Series Switches Typical Configuration Examples 5. 2 Comprehensive Configuration Examples Configure security functions, such as security policies and IPS on NGFW Module_A. NGFW Module_A will automatically synchronize its configurations to NGFW Module_B. Procedure Step 1 Complete interface and basic network configurations on NGFW Modules. # Configure device name on NGFW Module_A. <sysname> system-view [sysname] sysname Module_A # Create VLANs on NGFW Module_A. [Module_A] vlan batch 200 301 to 302 [Module_A-vlan-302] quit # Create Layer-2 Eth-Trunk 1 on NGFW Module_A and permit packets from the upstream and downstream VLANs. [Module_A] interface Eth-Trunk 1 [Module_A-Eth-Trunk1] description To_SwitchA_trunk10 [Module_A-Eth-Trunk1] portswitch [Module_A-Eth-Trunk1] port link-type trunk [Module_A-Eth-Trunk1] port trunk permit vlan 200 301 to 302 [Module_A-Eth-Trunk1] quit # Add the interfaces connecting NGFW Module_A to its connected switch to EthTrunk 1. [Module_A] interface GigabitEthernet 1/0/0 [Module_A-GigabitEthernet1/0/0] portswitch [Module_A-GigabitEthernet1/0/0] Eth-Trunk 1 [Module_A-GigabitEthernet1/0/0] quit [Module_A] interface GigabitEthernet 1/0/1 [Module_A-GigabitEthernet1/0/1] portswitch [Module_A-GigabitEthernet1/0/1] Eth-Trunk 1 [Module_A-GigabitEthernet1/0/1] quit # Configure Eth-Trunk 1 as an interface pair on NGFW Module_A. [Module_A] pair-interface Eth-Trunk 1 Eth-Trunk 1 # Add the two interfaces on the panel of NGFW Module_A to Eth-Trunk 0. [Module_A] interface Eth-Trunk 0 [Module_A-Eth-Trunk0] description hrp_interface [Module_A-Eth-Trunk0] ip address 10.10.0.1 24 [Module_A-Eth-Trunk0] quit [Module_A] interface GigabitEthernet 0/0/1 [Module_A-GigabitEthernet0/0/1] Eth-Trunk 0 [Module_A-GigabitEthernet0/0/1] quit [Module_A] interface GigabitEthernet 0/0/2 [Module_A-GigabitEthernet0/0/2] Eth-Trunk 0 [Module_A-GigabitEthernet0/0/2] quit # Assign the interfaces of NGFW Module_A to security zones. [Module_A] firewall zone trust [Module_A-zone-trust] add interface Eth-Trunk 1 [Module_A-zone-trust] quit [Module_A] firewall zone name hrp [Module_A-zone-hrp] set priority 75 [Module_A-zone-hrp] add interface Eth-Trunk 0 [Module_A-zone-hrp] quit # Configure device name on NGFW Module_B. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 27 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples <sysname> system-view [sysname] sysname Module_B # Create VLANs on NGFW Module_B. [Module_B] vlan batch 200 301 to 302 [Module_B-vlan-302] quit # Create Layer-2 Eth-Trunk 1 on NGFW Module_B and permit packets from the upstream and downstream VLANs. [Module_B] interface Eth-Trunk 1 [Module_B-Eth-Trunk1] description To_SwitchB_trunk10 [Module_B-Eth-Trunk1] portswitch [Module_B-Eth-Trunk1] port link-type trunk [Module_B-Eth-Trunk1] port trunk permit vlan 200 301 to 302 [Module_B-Eth-Trunk1] quit # Add the interfaces connecting NGFW Module_B to its connected switch to EthTrunk 1. [Module_B] interface GigabitEthernet 1/0/0 [Module_B-GigabitEthernet1/0/0] portswitch [Module_B-GigabitEthernet1/0/0] Eth-Trunk 1 [Module_B-GigabitEthernet1/0/0] quit [Module_B] interface GigabitEthernet 1/0/1 [Module_B-GigabitEthernet1/0/1] portswitch [Module_B-GigabitEthernet1/0/1] Eth-Trunk 1 [Module_B-GigabitEthernet1/0/1] quit # Configure Eth-Trunk 1 as an interface pair on NGFW Module_B. [Module_B] pair-interface Eth-Trunk 1 Eth-Trunk 1 # Add the two interfaces on the panel of NGFW Module_B to Eth-Trunk 0. [Module_B] interface Eth-Trunk 0 [Module_B-Eth-Trunk0] description hrp_interface [Module_B-Eth-Trunk0] ip address 10.10.0.2 24 [Module_B-Eth-Trunk0] quit [Module_B] interface GigabitEthernet 0/0/1 [Module_B-GigabitEthernet0/0/1] Eth-Trunk 0 [Module_B-GigabitEthernet0/0/1] quit [Module_B] interface GigabitEthernet 0/0/2 [Module_B-GigabitEthernet0/0/2] Eth-Trunk 0 [Module_B-GigabitEthernet0/0/2] quit # Assign the interfaces of NGFW Module_B to security zones. [Module_B] firewall zone trust [Module_B-zone-trust] add interface Eth-Trunk 1 [Module_B-zone-trust] quit [Module_B] firewall zone name hrp [Module_B-zone-hrp] set priority 75 [Module_B-zone-hrp] add interface Eth-Trunk 0 [Module_B-zone-hrp] quit Step 2 Configure hot standby on NGFW Modules. # Enable quick session backup on NGFW Module_A. [Module_A] hrp mirror session enable # Specify the heartbeat interface and enable hot standby on NGFW Module_A. [Module_A] hrp interface Eth-Trunk 0 [Module_A] hrp enable [Module_A] hrp loadbalance-device //This command is required only in versions earlier than V100R001C30SPC300. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 28 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples # Enable quick session backup on NGFW Module_B. [Module_B] hrp mirror session enable # Specify the heartbeat interface and enable hot standby on NGFW Module_B. [Module_B] hrp interface Eth-Trunk 0 [Module_B] hrp enable [Module_B] hrp loadbalance-device //This command is required only in versions earlier than V100R001C30SPC300. NOTE After hot standby is configured, the configurations and sessions on the active device are synchronized to the standby device; therefore, you only need to perform the following configurations on the active NGFW Module_A. Before configuring intrusion prevention, ensure that the required license is loaded and the intrusion prevention signature database is the latest version. When configuring intrusion prevention, use the default intrusion prevention profile default. Step 3 Configure security services on NGFW Modules. # On NGFW Module_A, configure a security policy to allow intranet users to access the Internet and configure intrusion prevention. HRP_A[Module_A] security-policy HRP_A[Module_A-policy-security] rule name policy_to_wan HRP_A[Module_A-policy-security-rule-policy_to_wan] source-address 10.1.0.0 24 HRP_A[Module_A-policy-security-rule-policy_to_wan] source-address 10.2.0.0 24 HRP_A[Module_A-policy-security-rule-policy_to_wan] profile ips default HRP_A[Module_A-policy-security-rule-policy_to_wan] action permit HRP_A[Module_A-policy-security-rule-policy_to_wan] quit HRP_A[Module_A-policy-security] quit NOTE In this example, the configured security policy allows intranet users to access the Internet. To enable the Internet to access the intranet, configure a rule whose the destination address is an intranet address. # Configure ASPF on NGFW Module_A. FTP is used as an example. HRP_A[Module_A] firewall zone trust HRP_A[Module_A-zone-trust] detect ftp HRP_A[Module_A-zone-trust] quit # Save configurations on NGFW Module_A and NGFW Module_B. HRP_A<Module_A> save The current configurations will be written to the device. Are you sure?[Y/N] y Now saving the current configuration to the device...... Info:The Current Configuration was saved to the device successfully HRP_S<Module_B> save The current configurations will be written to the device. Are you sure?[Y/N] y Now saving the current configuration to the device...... Info:The Current Configuration was saved to the device successfully Step 4 Configure the core switches to form a CSS. 1. Install the hardware and connect the cables. For details, see the CSS Installation Guide. 2. Set the CSS connection mode (such as the CSS card connection mode), CSS ID, and CSS priority. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 29 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples # Configure the CSS on SwitchA. In the example, the CSS connection mode is CSS card connection mode, the CSS ID is 1, and the CSS priority is 100. <Huawei> system-view [Huawei] sysname SwitchA [SwitchA] set css mode css-card card connection mode. [SwitchA] set css id 1 [SwitchA] set css priority 100 //Set the CSS connection mode. The default mode is CSS //Set the CSS ID. The default value is 1. //Set the CSS priority. The default value is 1. # Configure the CSS on SwitchB. In the example, the CSS connection mode is CSS card connection mode, the CSS ID is 2, and the CSS priority is 10. <Huawei> system-view [Huawei] sysname SwitchB [SwitchB] set css mode css-card [SwitchB] set css id 2 [SwitchB] set css priority 10 3. Enable the CSS function. # To use SwitchA as the active switch, enable CSS on SwitchA and then restart SwitchA. [SwitchA] css enable Warning: The CSS configuration will take effect only after the system is rebooted. T he next CSS mode is CSS card. Reboot now? [Y/N]:y # Enable CSS on SwitchB and then restart SwitchB. [SwitchB] css enable Warning: The CSS configuration will take effect only after the system is rebooted. T he next CSS mode is CSS card. Reboot now? [Y/N]:y 4. Check whether the CSS is established. # Log in to the CSS from the console port of any MPU and run the following command to view the CSS status. <SwitchA> display css status CSS Enable switch On Chassis Id CSS Enable CSS Status CSS Mode Priority Master Force -----------------------------------------------------------------------------Off 1 On Master CSS card 100 2 On Standby CSS card 10 Off If the CSS IDs, CSS priorities, CSS enabling status, and CSS status of the two member switches are displayed, as shown in the preceding information, the CSS has been established. You are advised to configure MAD to minimize the impact of a CSS split on services. Detailed configurations will not be described here. 5. Rename the cluster system to CSS. <SwitchA> system-view [SwitchA] sysname CSS [CSS] Step 5 Configure switch interfaces and VLANs. This example describes how to configure interoperation between the switch and NGFW modules. 1. Create VLANs. [CSS] vlan batch 200 301 to 302 2. Issue 34 (2022-10-26) Configure upstream and downstream interfaces, isolate the upstream and downstream interfaces from Eth-Trunk10 unidirectionally. Adding the interfaces to Eth-Trunk interfaces is not mentioned here. Copyright © Huawei Technologies Co., Ltd. 30 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [CSS] interface eth-trunk 2 [CSS-Eth-Trunk2] port link-type trunk [CSS-Eth-Trunk2] undo port trunk allow-pass vlan 1 [CSS-Eth-Trunk2] port trunk allow-pass vlan 301 [CSS-Eth-Trunk2] am isolate Eth-Trunk 10 [CSS-Eth-Trunk2] quit [CSS] interface eth-trunk 3 [CSS-Eth-Trunk3] port link-type trunk [CSS-Eth-Trunk3] undo port trunk allow-pass vlan 1 [CSS-Eth-Trunk3] port trunk allow-pass vlan 302 [CSS-Eth-Trunk3] am isolate Eth-Trunk 10 [CSS-Eth-Trunk3] quit [CSS] interface eth-trunk 5 [CSS-Eth-Trunk5] port link-type access [CSS-Eth-Trunk5] port default vlan 200 [CSS-Eth-Trunk5] am isolate Eth-Trunk 10 [CSS-Eth-Trunk5] quit 3. Configure VLANIF interfaces as upstream and downstream gateways. [CSS] interface vlanif301 [CSS-Vlanif301] ip address 10.1.0.1 24 [CSS-Vlanif301] quit [CSS] interface vlanif302 [CSS-Vlanif302] ip address 10.2.0.1 24 [CSS-Vlanif302] quit [CSS] interface vlanif200 [CSS-Vlanif200] ip address 10.3.0.1 24 [CSS-Vlanif200] quit 4. Add the switch interfaces connected to NGFW Module to Eth-Trunk 10. [CSS] interface eth-trunk 10 [CSS-Eth-Trunk10] description To_Module [CSS-Eth-Trunk10] port link-type trunk [CSS-Eth-Trunk10] trunkport xgigabitethernet 1/1/0/0 to 1/1/0/1 [CSS-Eth-Trunk10] trunkport xgigabitethernet 2/1/0/0 to 2/1/0/1 [CSS-Eth-Trunk10] undo port trunk allow-pass vlan 1 [CSS-Eth-Trunk10] port trunk allow-pass vlan 200 301 to 302 [CSS-Eth-Trunk10] mac-address learning disable [CSS-Eth-Trunk10] undo local-preference enable [CSS-Eth-Trunk10] stp disable [CSS-Eth-Trunk10] quit 5. Set the load balancing mode of the Eth-Trunk interface. NOTE When traffic is forwarded from the switches to the NGFW Modules, the cross-board EthTrunk distributes the traffic. To ensure that forward and return packets are forwarded by the same NGFW Module, set the enhanced load balancing mode. In the example, the source and destination IP addresses are used for illustration. [CSS] load-balance-profile module [CSS-load-balance-profile-module] ipv4 field sip dip [CSS-load-balance-profile-module] quit [CSS] interface Eth-Trunk 10 [CSS-Eth-Trunk10] load-balance enhanced profile module [CSS-Eth-Trunk10] quit 6. Configure traffic policies to redirect traffic to the NGFW Modules. # Create ACLs. [CSS] acl 3001 //Match traffic exchanged between intranet users of different VLANs. [CSS-acl-adv-3001] rule permit ip source 10.1.0.0 0.0.0.255 destination 10.2.0.0 0.0.0.255 [CSS-acl-adv-3001] rule permit ip source 10.2.0.0 0.0.0.255 destination 10.1.0.0 0.0.0.255 [CSS-acl-adv-3001] quit [CSS] acl 3002 //Match traffic sent by intranet users to access the Internet. [CSS-acl-adv-3002] rule permit ip source 10.1.0.0 0.0.0.255 [CSS-acl-adv-3002] rule permit ip source 10.2.0.0 0.0.0.255 [CSS-acl-adv-3002] quit Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 31 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [CSS] acl 3004 //Match traffic from the Internet to the intranet. [CSS-acl-adv-3004] rule permit ip destination 10.1.0.0 0.0.0.255 [CSS-acl-adv-3004] rule permit ip destination 10.2.0.0 0.0.0.255 [CSS-acl-adv-3004] quit # Configure the switch not to direct the traffic exchanged between intranet users but to direct traffic sent by the intranet to access the Internet to the NGFW Modules. [CSS] traffic classifier classifier1 precedence 5 [CSS-classifier-classifier1] if-match acl 3001 [CSS-classifier-classifier1] quit [CSS] traffic behavior behavior1 //Permit traffic exchanged between intranet users. [CSS-behavior-behavior1] permit [CSS-behavior-behavior1] quit [CSS] traffic classifier classifier2 precedence 10 [CSS-classifier-classifier2] if-match acl 3002 [CSS-classifier-classifier2] quit [CSS] traffic behavior behavior2 //Redirect the traffic from the intranet to the Internet to the interface connecting the switch to the NGFW Module. [CSS-behavior-behavior2] redirect interface Eth-Trunk 10 [CSS-behavior-behavior2] quit //Configure a traffic policy. [CSS] traffic policy policy1 [CSS-trafficpolicy-policy1] classifier classifier1 behavior behavior1 [CSS-trafficpolicy-policy1] classifier classifier2 behavior behavior2 [CSS-trafficpolicy-policy1] quit [CSS] interface Eth-Trunk 2 [CSS-Eth-Trunk2] traffic-policy policy1 inbound [CSS-Eth-Trunk2] quit [CSS] interface Eth-Trunk 3 [CSS-Eth-Trunk3] traffic-policy policy1 inbound [CSS-Eth-Trunk3] quit # Configure the switch to redirect the traffic from the Internet to the intranet to the NGFW Module. [CSS] traffic classifier classifier4 [CSS-classifier-classifier4] if-match acl 3004 [CSS-classifier-classifier4] quit //Redirect the traffic from the Internet to the intranet to the [CSS] traffic behavior behavior4 interface connecting the switch to the NGFW Module. [CSS-behavior-behavior4] redirect interface Eth-Trunk 10 [CSS-behavior-behavior4] quit //Configure a traffic policy. [CSS] traffic policy policy2 [CSS-trafficpolicy-policy2] classifier classifier4 behavior behavior4 [CSS-trafficpolicy-policy2] quit [CSS] interface Eth-Trunk 5 [CSS-Eth-Trunk5] traffic-policy policy2 inbound [CSS-Eth-Trunk5] quit 7. Configure a static route. NOTE After receiving packets, the switch looks up the routing table to complete Layer-3 forwarding although redirection policies are configured. However, the outgoing interfaces of packets are still determined by the redirection policies. In the example, when receiving a packet from the intranet to the Internet, the switch first looks up the routing table, changes the VLAN tag from 301 or 302 to 200 based on the default route, and then forwards the packet to the NGFW Module. After receiving a packet from the Internet to the intranet, the switch changes the VLAN tag from 200 to 301 or 302 based on the direct route and then forwards the packet to the NGFW Module. If no routing entry is matched, the switch forwards the packet based on the redirection policy without changing the VLAN tag. # Configure a default route to the Internet. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 32 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [CSS] ip route-static 0.0.0.0 0.0.0.0 10.3.0.5 ----End Verification 1. Run the display hrp state command on NGFW Module_A to check the current HRP status. If the following output is displayed, an HRP relationship is successfully established. HRP_A[Module_A] display hrp state The firewall's config state is: ACTIVE Backup channel usage: 0.01% Time elapsed after the last switchover: 0 days, 0 hours, 36 minutes Current state of interfaces tracked by active: Eth-trunk1 (VLAN 200) : up Eth-trunk1 (VLAN 301) : up Eth-trunk1 (VLAN 302) : up Current state of interfaces tracked by standby: Eth-trunk1 (VLAN 200) : up Eth-trunk1 (VLAN 301) : up Eth-trunk1 (VLAN 302) : up 2. Check whether the access from the intranet to the Internet succeeds and check the session table of each NGFW Module. HRP_A[Module_A] display firewall session table Current Total Sessions : 1 http VPN: public --> public 10.1.0.10:22048 --> 3.3.3.3:80 HRP_S[Module_B] display firewall session table Current Total Sessions : 1 http VPN: public --> public Remote 10.1.0.10:22048 --> 3.3.3.3:80 According to the preceding output, NGFW Module_A has created a session entry for the access from the intranet to the Internet. A session entry with the Remote tag exists on NGFW Module_B, which indicates that session backup succeeds after you configure hot standby. 3. Configure a PC in the Trust zone to constantly ping the public address and run the shutdown command on Eth-trunk1 of NGFW Module_A. Then check the status switchover of the NGFW Module and discarded ping packets. If the status switchover is normal, NGFW Module_B becomes the active and carries services. No or several ping packets (1 to 3 packets, depending on actual network environments) are discarded. Run the undo shutdown command on Eth-trunk1 of NGFW Module_A and check the status switchover of the NGFW Module and discarded ping packets. If the status switchover is normal, NGFW Module_A becomes the active and starts to carry service after the preemption delay (60s by default) expires. No or several ping packets (1 to 3 packets, depending on actual network environments) are discarded. Configuration Scripts Configuration scripts of the NGFW Modules: Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 33 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples NGFW Module_A NGFW Module_B # sysname Module_A # hrp mirror session enable hrp enable hrp interface Eth-Trunk0 hrp loadbalance-device //This command is required only in versions earlier than V100R001C30SPC300. # vlan batch 200 301 to 302 # pair-interface Eth-Trunk1 Eth-Trunk1 # vlan 200 hrp track active hrp track standby Eth-Trunk1 # vlan 301 hrp track active hrp track standby Eth-Trunk1 # vlan 302 hrp track active hrp track standby Eth-Trunk1 # interface Eth-Trunk0 description hrp_interface ip address 10.10.0.1 255.255.255.0 # interface Eth-Trunk1 description To_SwitchA_trunk10 portswitch port link-type trunk port trunk permit vlan 200 301 to 302 # interface GigabitEthernet0/0/1 eth-trunk 0 # interface GigabitEthernet0/0/2 eth-trunk 0 # interface GigabitEthernet1/0/0 portswitch eth-trunk 1 # interface GigabitEthernet1/0/1 portswitch eth-trunk 1 # firewall zone trust set priority 85 detect ftp add interface Eth-Trunk1 # firewall zone name hrp set priority 75 add interface Eth-Trunk0 # security-policy rule name policy_to_wan source-address 10.1.0.0 mask 255.255.255.0 source-address 10.2.0.0 mask 255.255.255.0 # sysname Module_B # hrp mirror session enable hrp enable hrp interface Eth-Trunk0 hrp loadbalance-device //This command is required only in versions earlier than V100R001C30SPC300. # vlan batch 200 301 to 302 # pair-interface Eth-Trunk1 Eth-Trunk1 # vlan 200 hrp track active hrp track standby Eth-Trunk1 # vlan 301 hrp track active hrp track standby Eth-Trunk1 # vlan 302 hrp track active hrp track standby Eth-Trunk1 # interface Eth-Trunk0 description hrp_interface ip address 10.10.0.2 255.255.255.0 # interface Eth-Trunk1 description To_SwitchB_trunk10 portswitch port link-type trunk port trunk permit vlan 200 301 to 302 # interface GigabitEthernet0/0/1 eth-trunk 0 # interface GigabitEthernet0/0/2 eth-trunk 0 # interface GigabitEthernet1/0/0 portswitch eth-trunk 1 # interface GigabitEthernet1/0/1 portswitch eth-trunk 1 # firewall zone trust set priority 85 detect ftp add interface Eth-Trunk1 # firewall zone name hrp set priority 75 add interface Eth-Trunk0 # security-policy rule name policy_to_wan source-address 10.1.0.0 mask 255.255.255.0 source-address 10.2.0.0 mask 255.255.255.0 Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 34 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples NGFW Module_A NGFW Module_B profile ips default action permit # return profile ips default action permit # return Configuration script of CSS: # ----Traffic diversion configuration---load-balance-profile module # vlan batch 200 301 to 302 # acl number 3001 rule 5 permit ip source 10.1.0.0 0.0.0.255 destination 10.2.0.0 0.0.0.255 rule 10 permit ip source 10.2.0.0 0.0.0.255 destination 10.1.0.0 0.0.0.255 acl number 3002 rule 5 permit ip source 10.1.0.0 0.0.0.255 rule 10 permit ip source 10.2.0.0 0.0.0.255 acl number 3004 rule 5 permit ip destination 10.1.0.0 0.0.0.255 rule 10 permit ip destination 10.2.0.0 0.0.0.255 # traffic classifier classifier1 operator or precedence 5 if-match acl 3001 traffic classifier classifier2 operator or precedence 10 if-match acl 3002 traffic classifier classifier4 operator or precedence 15 if-match acl 3004 # traffic behavior behavior1 permit traffic behavior behavior2 permit redirect interface Eth-Trunk10 traffic behavior behavior4 permit redirect interface Eth-Trunk10 # traffic policy policy1 match-order config classifier classifier1 behavior behavior1 classifier classifier2 behavior behavior2 traffic policy policy2 match-order config classifier classifier4 behavior behavior4 # interface Vlanif200 ip address 10.3.0.1 255.255.255.0 # interface Vlanif301 ip address 10.1.0.1 255.255.255.0 # interface Vlanif302 ip address 10.2.0.1 255.255.255.0 # interface Eth-Trunk2 port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 301 am isolate Eth-Trunk 10 traffic-policy policy1 inbound # interface Eth-Trunk3 port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 302 Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 35 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples am isolate Eth-Trunk 10 traffic-policy policy1 inbound # interface Eth-Trunk5 port default vlan 200 am isolate Eth-Trunk 10 traffic-policy policy2 inbound # interface Eth-Trunk10 description To_Module port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 200 301 to 302 mac-address learning disable stp disable load-balance enhanced profile module undo local-preference enable # interface XGigabitEthernet1/1/0/0 eth-trunk 10 # interface XGigabitEthernet1/1/0/1 eth-trunk 10 # interface xgigabitethernet1/1/0/2 eth-trunk 2 # interface xgigabitethernet1/1/0/3 eth-trunk 3 # interface xgigabitethernet1/1/0/5 eth-trunk 5 # interface XGigabitEthernet2/1/0/0 eth-trunk 10 # interface XGigabitEthernet2/1/0/1 eth-trunk 10 # interface xgigabitethernet2/1/0/2 eth-trunk 2 # interface xgigabitethernet2/1/0/3 eth-trunk 3 # interface xgigabitethernet2/1/0/5 eth-trunk 5 # ip route-static 0.0.0.0 0.0.0.0 10.3.0.5 # return 2.3.2 Layer 3 Active/Standby Hot Standby on the NGFW Modules Installed on a Cluster Switch Where Static Routebased Traffic Diversion Is Implemented Service Requirements As shown in Figure 2-7, two switches are deployed in a CSS and two NGFW Modules are installed in slot 1 on the two switches. The two NGFW Modules are required to implement hot standby and perform security detection on traffic passing through the switches. Two NGFW Modules work in active/standby mode. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 36 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples This example uses NGFW modules running V100R001C30 and switches running V200R008C00. For the configuration examples of NGFW Modules running other versions, see Deployment Guide. Figure 2-7 Networking for Layer-3 dual-NGFW Module deployment and switch CSS NOTE The NGFW Module has two fixed internal Ethernet interfaces: GE1/0/0 to GE1/0/1. The numbering of internal Ethernet interfaces on the switch is determined by the slot in which the NGFW Module is installed. For example, when the NGFW Module is installed in slot 1 on the switch, the internal Ethernet interfaces used by the switch are XGE1/1/0/0 to XGE1/1/0/1. Eth-Trunk2 and Eth-Trunk3 are interfaces of the switches in the CSS. Data Planning Item Data Description Hot standby NGFW Module_A: active - NGFW Module_B: standby NAT Issue 34 (2022-10-26) Source NAT NAT type: PAT Address pool: 1.1.1.1 to 1.1.1.2 The source address is automatically translated for Internet access from a specified private subnet. Copyright © Huawei Technologies Co., Ltd. 37 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Item NAT Server Data Description Global address: 1.1.1.3 A specified server address is translated from a private address to a public address for Internet users to access. Inside address: 192.168.2.8 Securit y policy Policy 1: policy_sec1 Source security zone: Trust Destination security zone: Untrust Users in the Trust zone (residing on 192.168.1.0/24) are allowed to access the Internet. Source IP address: 192.168.1.0 Action: permit Policy 2: policy_sec2 Source security zone: Untrust Destination security zone: DMZ Extranet users are allowed to access the DMZ (residing on 192.168.2.0/24), and intrusion prevention is implemented. Destination IP address: 192.168.2.0 Action: permit Deployment Solution 1. Two NGFW Modules form hot standby networking. The switch diverts the passing traffic to the NGFW Module through a static route. After performing security check on the traffic, the NGFW Module rejects the traffic to the switch through a static route. Configure VRF on the switches to virtualize the switches as virtual switch Public connecting to the public network (no VPN instance needs to be configured) and virtual switches trust and dmz respectively connecting to the Trust zone and DMZ. Figure 2-8 shows the networking. The virtual switches are separated. Therefore, traffic will be forwarded to the NGFW Modules. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 38 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Figure 2-8 Configuring VRF on switches 2. Figure 2-8 can be abstracted as Figure 2-9. The NGFW Modules run static routes with upstream and downstream devices. Therefore, you need to configure VRRP groups on the NGFW Modules, so that the switches communicate with the virtual IP addresses of VRRP groups on the NGFW Modules. Configure a default route to the Internet on the NGFW Module, and set the next-hop address to the IP address of VLANIF201. Configure a specific route to the intranet on the NGFW Module, and set the next-hop address to the IP address of VLANIF202. Figure 2-9 shows the networking. On the virtual switch Public, configure static routes to the Trust zone and DMZ and set the next-hop address to the IP address of VRRP group 1. On the virtual switch trust, configure a default route to the Internet and set the next-hop address to the IP address of VRRP group 2. On the virtual switch dmz, configure a default route to the Internet and set the next-hop address to the IP address of VRRP group 3. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 39 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Figure 2-9 Configuring VRRP groups on the NGFW Modules and static routes on the switches NOTE Figure 2-9 lists only the switch interfaces involved in the connection with the NGFW Modules. 3. Bundle GE0/0/1 and GE0/0/2 interfaces on the panel of each NGFW Module into an Eth-Trunk0 interface, which functions as the heartbeat interface and backup channel and enable hot standby. 4. Configure security functions, such as security policies, nat policies, and IPS on NGFW Module_A. NGFW Module_A will automatically synchronize its configurations to NGFW Module_B. Procedure Step 1 Complete interface and basic network configurations on NGFW Modules. # Configure device name on NGFW Module_A. <sysname> system-view [sysname] sysname Module_A # Configure IP addresses for the interfaces on NGFW Module_A. [Module_A] interface Eth-trunk 1 [Module_A-Eth-Trunk1] quit [Module_A] interface GigabitEthernet 1/0/0 [Module_A-GigabitEthernet1/0/0] Eth-Trunk 1 [Module_A-GigabitEthernet1/0/0] quit [Module_A] interface GigabitEthernet 1/0/1 [Module_A-GigabitEthernet1/0/1] Eth-Trunk 1 [Module_A-GigabitEthernet1/0/1] quit [Module_A] interface Eth-trunk 1.1 [Module_A-Eth-Trunk1.1] ip address 10.3.1.2 24 [Module_A-Eth-Trunk1.1] vlan-type dot1q 201 [Module_A-Eth-Trunk1.1] quit Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 40 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [Module_A] interface Eth-trunk 1.2 [Module_A-Eth-Trunk1.2] ip address 10.3.2.2 24 [Module_A-Eth-Trunk1.2] vlan-type dot1q 202 [Module_A-Eth-Trunk1.2] quit [Module_A] interface Eth-trunk 1.3 [Module_A-Eth-Trunk1.3] ip address 10.3.3.2 24 [Module_A-Eth-Trunk1.3] vlan-type dot1q 203 [Module_A-Eth-Trunk1.3] quit [Module_A] interface Eth-Trunk 0 [Module_A-Eth-Trunk0] ip address 10.10.0.1 24 [Module_A-Eth-Trunk0] quit [Module_A] interface GigabitEthernet 0/0/1 [Module_A-GigabitEthernet0/0/1] Eth-Trunk 0 [Module_A-GigabitEthernet0/0/1] quit [Module_A] interface GigabitEthernet 0/0/2 [Module_A-GigabitEthernet0/0/2] Eth-Trunk 0 [Module_A-GigabitEthernet0/0/2] quit # Assign the interfaces of NGFW Module_A to security zones. [Module_A] firewall zone untrust [Module_A-zone-untrust] add interface Eth-trunk 1.1 [Module_A-zone-untrust] quit [Module_A] firewall zone trust [Module_A-zone-trust] add interface Eth-trunk 1.2 [Module_A-zone-trust] quit [Module_A] firewall zone dmz [Module_A-zone-dmz] add interface Eth-trunk 1.3 [Module_A-zone-dmz] quit [Module_A] firewall zone name hrpzone [Module_A-zone-hrpzone] set priority 65 [Module_A-zone-hrpzone] add interface Eth-Trunk 0 [Module_A-zone-hrpzone] quit # Configure device name on NGFW Module_B. <sysname> system-view [sysname] sysname Module_B # Configure IP addresses for the interfaces on NGFW Module_B. [Module_B] interface Eth-Trunk 1 [Module_B-Eth-Trunk1] quit [Module_B] interface GigabitEthernet 1/0/0 [Module_B-GigabitEthernet1/0/0] Eth-Trunk 1 [Module_B-GigabitEthernet1/0/0] quit [Module_B] interface GigabitEthernet 1/0/1 [Module_B-GigabitEthernet1/0/1] Eth-Trunk 1 [Module_B-GigabitEthernet1/0/1] quit [Module_B] interface Eth-trunk 1.1 [Module_B-Eth-Trunk1.1] ip address 10.3.1.3 24 [Module_B-Eth-Trunk1.1] vlan-type dot1q 201 [Module_B-Eth-Trunk1.1] quit [Module_B] interface Eth-trunk 1.2 [Module_B-Eth-Trunk1.2] ip address 10.3.2.3 24 [Module_B-Eth-Trunk1.2] vlan-type dot1q 202 [Module_B-Eth-Trunk1.2] quit [Module_B] interface Eth-trunk 1.3 [Module_B-Eth-Trunk1.3] ip address 10.3.3.3 24 [Module_B-Eth-Trunk1.3] vlan-type dot1q 203 [Module_B-Eth-Trunk1.3] quit [Module_B] interface Eth-Trunk 0 [Module_B-Eth-Trunk0] ip address 10.10.0.2 24 [Module_B-Eth-Trunk0] quit [Module_B] interface GigabitEthernet 0/0/1 [Module_B-GigabitEthernet0/0/1] Eth-Trunk 0 [Module_B-GigabitEthernet0/0/1] quit [Module_B] interface GigabitEthernet 0/0/2 [Module_B-GigabitEthernet0/0/2] Eth-Trunk 0 [Module_B-GigabitEthernet0/0/2] quit Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 41 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples # Assign the interfaces of NGFW Module_B to security zones. [Module_B] firewall zone untrust [Module_B-zone-untrust] add interface Eth-trunk 1.1 [Module_B-zone-untrust] quit [Module_B] firewall zone trust [Module_B-zone-trust] add interface Eth-trunk 1.2 [Module_B-zone-trust] quit [Module_B] firewall zone dmz [Module_B-zone-dmz] add interface Eth-trunk 1.3 [Module_B-zone-dmz] quit [Module_B] firewall zone name hrpzone [Module_B-zone-hrpzone] set priority 65 [Module_B-zone-hrpzone] add interface Eth-Trunk 0 [Module_B-zone-hrpzone] quit Step 2 Create static routes on NGFW Modules. # On NGFW Module_A, configure an upstream static route (default route) with the next-hop address set to the IP address of VLANIF201. [Module_A] ip route-static 0.0.0.0 0.0.0.0 10.3.1.4 # On NGFW Module_A, configure a downstream static route to the Trust zone, with the destination address being the address of the Trust zone and next-hop address being the address of VLANIF202 on the connected switch. [Module_A] ip route-static 192.168.1.0 255.255.255.0 10.3.2.4 # On NGFW Module_A, configure a downstream static route to the DMZ, with the destination address being the address of the DMZ and next-hop address being the address of VLANIF203 on the connected switch. [Module_A] ip route-static 192.168.2.0 255.255.255.0 10.3.3.4 # On NGFW Module_A, configure a black-hole route to an address in the source NAT address pool to prevent routing loops. In this example, the address range is 1.1.1.1-1.1.1.2 in the source NAT address pool. [Module_A] ip route-static 1.1.1.1 255.255.255.255 null 0 [Module_A] ip route-static 1.1.1.2 255.255.255.255 null 0 # On NGFW Module_A, configure a black-hole route to the global address of the NAT server to prevent routing loops. In this example, the global address of the NAT server is 1.1.1.3. [Module_A] ip route-static 1.1.1.3 255.255.255.255 null 0 # On NGFW Module_B, configure an upstream static route (default route) with the next-hop address set to the IP address of VLANIF201 on the connected switch. [Module_B] ip route-static 0.0.0.0 0.0.0.0 10.3.1.4 # On NGFW Module_B, configure a downstream static route to the Trust zone, with the destination address being the address of the Trust zone and next-hop address being the address of VLANIF202 on the connected switch. [Module_B] ip route-static 192.168.1.0 255.255.255.0 10.3.2.4 # On NGFW Module_B, configure a downstream static route to the DMZ, with the destination address being the address of the DMZ and next-hop address being the address of VLANIF203 on the connected switch. [Module_B] ip route-static 192.168.2.0 255.255.255.0 10.3.3.4 Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 42 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples # On NGFW Module_B, configure a black-hole route to an address in the source NAT address pool to prevent routing loops. In this example, the address range is 1.1.1.1-1.1.1.2 in the source NAT address pool. [Module_B] ip route-static 1.1.1.1 255.255.255.255 null 0 [Module_B] ip route-static 1.1.1.2 255.255.255.255 null 0 # On NGFW Module_B, configure a black-hole route to the global address of the NAT server to prevent routing loops. In this example, the global address of the NAT server is 1.1.1.3. [Module_B] ip route-static 1.1.1.3 255.255.255.255 null 0 Step 3 Configure hot standby on NGFW Modules. # Configure VRRP groups on NGFW Module_A. [Module_A] interface Eth-trunk1.1 [Module_A-Eth-Trunk1.1] vrrp vrid 1 virtual-ip 10.3.1.1 active [Module_A-Eth-Trunk1.1] quit [Module_A] interface Eth-trunk1.2 [Module_A-Eth-Trunk1.2] vrrp vrid 2 virtual-ip 10.3.2.1 active [Module_A-Eth-Trunk1.2] quit [Module_A] interface Eth-trunk1.3 [Module_A-Eth-Trunk1.3] vrrp vrid 3 virtual-ip 10.3.3.1 active [Module_A-Eth-Trunk1.3] quit # Specify the heartbeat interface and enable hot standby on NGFW Module_A. [Module_A] hrp interface Eth-Trunk 0 [Module_A] hrp enable # Configure VRRP groups on NGFW Module_B. [Module_B] interface Eth-trunk1.1 [Module_B-Eth-Trunk1.1] vrrp vrid 1 virtual-ip 10.3.1.1 standby [Module_B-Eth-Trunk1.1] quit [Module_B] interface Eth-trunk1.2 [Module_B-Eth-Trunk1.2] vrrp vrid 2 virtual-ip 10.3.2.1 standby [Module_B-Eth-Trunk1.2] quit [Module_B] interface Eth-trunk1.3 [Module_B-Eth-Trunk1.3] vrrp vrid 3 virtual-ip 10.3.3.1 standby [Module_B-Eth-Trunk1.3] quit # Specify the heartbeat interface and enable hot standby on NGFW Module_B. [Module_B] hrp interface Eth-Trunk 0 [Module_B] hrp enable [Module_B] hrp standby-device //This command is required only in versions earlier than V100R001C30SPC300. NOTE After hot standby is configured, the configurations and sessions on the active device are synchronized to the standby device; therefore, you only need to perform the following configurations on the active NGFW Module_A. Before configuring intrusion prevention, ensure that the required license is loaded and the intrusion prevention signature database is the latest version. When configuring intrusion prevention, use the default intrusion prevention profile default. Step 4 Configure security services on NGFW Modules. # On NGFW Module_A, configure a security policy to allow users in the Trust zone (network segment 192.168.1.0/24) to access the Internet. HRP_A[Module_A] security-policy HRP_A[Module_A-policy-security] rule name policy_sec1 Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 43 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples HRP_A[Module_A-policy-security-rule-policy_sec1] source-zone trust HRP_A[Module_A-policy-security-rule-policy_sec1] destination-zone untrust HRP_A[Module_A-policy-security-rule-policy-sec1] source-address 192.168.1.0 24 HRP_A[Module_A-policy-security-rule-policy_sec1] action permit HRP_A[Module_A-policy-security-rule-policy_sec1] quit # On NGFW Module_A, configure a security policy to allow extranet users to access the DMZ (network segment 192.168.2.0/24) and configure intrusion prevention. HRP_A[Module_A-policy-security] rule name policy_sec2 HRP_A[Module_A-policy-security-rule-policy_sec2] source-zone untrust HRP_A[Module_A-policy-security-rule-policy_sec2] destination-zone dmz HRP_A[Module_A-policy-security-rule-policy-sec2] destination-address 192.168.2.0 24 HRP_A[Module_A-policy-security-rule-policy_sec2] service http ftp HRP_A[Module_A-policy-security-rule-policy_sec2] profile ips default HRP_A[Module_A-policy-security-rule-policy_sec2] action permit HRP_A[Module_A-policy-security-rule-policy_sec2] quit HRP_A[Module_A-policy-security] quit # Configure ASPF on NGFW Module_A. FTP is used as an example. HRP_A[Module_A] firewall interzone untrust dmz HRP_A[Module_A-interzone-dmz-untrust] detect ftp HRP_A[Module_A-interzone-dmz-untrust] quit # Configure a NAT address pool. HRP_A[Module_A] nat address-group addressgroup1 HRP_A[Module_A-address-group-addressgroup1] section 0 1.1.1.1 1.1.1.2 HRP_A[Module_A-address-group-addressgroup1] quit # Configure a source NAT policy for Internet access from the specified private subnet. HRP_A[Module_A] nat-policy HRP_A[Module_A-policy-nat] rule name policy_nat1 HRP_A[Module_A-policy-nat-rule-policy_nat1] source-zone trust HRP_A[Module_A-policy-nat-rule-policy_nat1] destination-zone untrust HRP_A[Module_A-policy-nat-rule-policy_nat1] source-address 192.168.1.0 24 HRP_A[Module_A-policy-nat-rule-policy_nat1] action nat address-group addressgroup1 HRP_A[Module_A-policy-nat-rule-policy_nat1] quit HRP_A[Module_A-policy-nat] quit # Configure the NAT server function to translate the private address of a specific server in the DMZ into a public address for user access. In this example, private address 192.168.2.8:80 of the web server in the DMZ is translated into public address 1.1.1.3:8000. HRP_A[Module_A] nat server policy_web protocol tcp global 1.1.1.3 8000 inside 192.168.2.8 80 # Save configurations on NGFW Module_A and NGFW Module_B. HRP_A<Module_A> save The current configurations will be written to the device. Are you sure?[Y/N] y Now saving the current configuration to the device...... Info:The Current Configuration was saved to the device successfully HRP_S<Module_B> save The current configurations will be written to the device. Are you sure?[Y/N] y Now saving the current configuration to the device...... Info:The Current Configuration was saved to the device successfully Step 5 Configure the core switches to form a CSS. 1. Issue 34 (2022-10-26) Install the hardware and connect the cables. For details, see the CSS Installation Guide. Copyright © Huawei Technologies Co., Ltd. 44 Sx300 Series Switches Typical Configuration Examples 2. 2 Comprehensive Configuration Examples Set the CSS connection mode (such as the CSS card connection mode), CSS ID, and CSS priority. # Configure the CSS on SwitchA. In the example, the CSS connection mode is CSS card connection mode, the CSS ID is 1, and the CSS priority is 100. <Huawei> system-view [Huawei] sysname SwitchA [SwitchA] set css mode css-card card connection mode. [SwitchA] set css id 1 [SwitchA] set css priority 100 //Set the CSS connection mode. The default mode is CSS //Set the CSS ID. The default value is 1. //Set the CSS priority. The default value is 1. # Configure the CSS on SwitchB. In the example, the CSS connection mode is CSS card connection mode, the CSS ID is 2, and the CSS priority is 10. <Huawei> system-view [Huawei] sysname SwitchB [SwitchB] set css mode css-card [SwitchB] set css id 2 [SwitchB] set css priority 10 3. Enable the CSS function. # To use SwitchA as the active switch, enable CSS on SwitchA and then restart SwitchA. [SwitchA] css enable Warning: The CSS configuration will take effect only after the system is rebooted. T he next CSS mode is CSS card. Reboot now? [Y/N]:y # Enable CSS on SwitchB and then restart SwitchB. [SwitchB] css enable Warning: The CSS configuration will take effect only after the system is rebooted. T he next CSS mode is CSS card. Reboot now? [Y/N]:y 4. Check whether the CSS is established. # Log in to the CSS from the console port of any MPU and run the following command to view the CSS status. <SwitchA> display css status CSS Enable switch On Chassis Id CSS Enable CSS Status CSS Mode Priority Master Force -----------------------------------------------------------------------------Off 1 On Master CSS card 100 2 On Standby CSS card 10 Off If the CSS IDs, CSS priorities, CSS enabling status, and CSS status of the two member switches are displayed, as shown in the preceding information, the CSS has been established. You are advised to configure MAD to minimize the impact of a CSS split on services. Detailed configurations will not be described here. 5. Rename the cluster system to CSS. <SwitchA> system-view [SwitchA] sysname CSS [CSS] Step 6 Configure interfaces and VLANs for core switches. This example describes how to configure interoperation between the switch and NGFW modules. [CSS] vlan batch 201 to 205 //Create VLANs. [CSS] interface eth-trunk 5 [CSS-Eth-Trunk5] description To_NGFW_Module_A Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 45 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [CSS-Eth-Trunk5] trunkport xgigabitethernet 1/1/0/0 to 1/1/0/1 //Create Eth-Trunk5 on the CSS and add internal Ethernet interfaces to Eth-Trunk5. [CSS-Eth-Trunk5] port link-type trunk [CSS-Eth-Trunk5] undo port trunk allow-pass vlan 1 [CSS-Eth-Trunk5] port trunk allow-pass vlan 201 to 205 //Configure Eth-Trunk5 to permit traffic from VLANs 201, 202, 203, 204, and 205. [CSS-Eth-Trunk5] quit [CSS] interface eth-trunk 6 [CSS-Eth-Trunk6] description To_NGFW_Module_B [CSS-Eth-Trunk6] trunkport xgigabitethernet 2/1/0/0 to 2/1/0/1 //Create Eth-Trunk6 on the CSS and add internal Ethernet interfaces to Eth-Trunk6. [CSS-Eth-Trunk6] port link-type trunk [CSS-Eth-Trunk6] undo port trunk allow-pass vlan 1 [CSS-Eth-Trunk6] port trunk allow-pass vlan 201 to 205 //Configure Eth-Trunk6 to permit traffic from VLANs 201, 202, 203, 204, and 205. [CSS-Eth-Trunk6] quit //Configure the switch interface Eth-Trunk2 that connects to the [CSS] interface eth-trunk 2 Trust zone, add the interfaces to Eth-Trunk2 is not mentioned here. [CSS-Eth-Trunk2] description To_TRUST [CSS-Eth-Trunk2] port link-type trunk [CSS-Eth-Trunk2] undo port trunk allow-pass vlan 1 [CSS-Eth-Trunk2] port trunk allow-pass vlan 204 //Enable Eth-Trunk2 to permit traffic from VLAN204. [CSS-Eth-Trunk2] quit //Configure the switch interface Eth-Trunk3 that connects to the [CSS] interface eth-trunk 3 DMZ, add the interfaces to Eth-Trunk3 is not mentioned here. [CSS-Eth-Trunk3] description To_DMZ [CSS-Eth-Trunk3] port link-type trunk [CSS-Eth-Trunk3] undo port trunk allow-pass vlan 1 [CSS-Eth-Trunk3] port trunk allow-pass vlan 205 //Enable Eth-Trunk3 to permit traffic from VLAN205. [CSS-Eth-Trunk3] quit [CSS] ip vpn-instance trust //Create VPN instance trust. [CSS-vpn-instance-trust] ipv4-family [CSS-vpn-instance-trust-af-ipv4] route-distinguisher 100:1 [CSS-vpn-instance-trust-af-ipv4] vpn-target 111:1 both [CSS-vpn-instance-trust-af-ipv4] quit [CSS-vpn-instance-trust] quit [CSS] ip vpn-instance dmz //Create VPN instance dmz. [CSS-vpn-instance-dmz] ipv4-family [CSS-vpn-instance-dmz-af-ipv4] route-distinguisher 200:1 [CSS-vpn-instance-dmz-af-ipv4] vpn-target 211:1 both [CSS-vpn-instance-dmz-af-ipv4] quit [CSS-vpn-instance-dmz] quit [CSS] interface vlanif 201 [CSS-Vlanif201] ip address 10.3.1.4 24 //Configure an IP address for VLANIF201. [CSS-Vlanif201] quit [CSS] interface vlanif 202 [CSS-Vlanif202] ip binding vpn-instance trust [CSS-Vlanif202] ip address 10.3.2.4 24 //Bind VLANIF202 to trust. //Configure an IP address for VLANIF202. [CSS-Vlanif202] quit [CSS] interface vlanif 203 [CSS-Vlanif203] ip binding vpn-instance dmz //Bind VLANIF203 to dmz. //Configure an IP address for VLANIF203. [CSS-Vlanif203] ip address 10.3.3.4 24 [CSS-Vlanif203] quit [CSS] interface vlanif 204 [CSS-Vlanif204] ip binding vpn-instance trust //Bind VLANIF204 to trust. //Configure an IP address for VLANIF204. [CSS-Vlanif204] ip address 10.1.1.2 24 [CSS-Vlanif204] quit [CSS] interface vlanif 205 [CSS-Vlanif205] ip binding vpn-instance dmz //Bind VLANIF205 to dmz. //Configure an IP address for VLANIF205. [CSS-Vlanif205] ip address 10.1.2.2 24 [CSS-Vlanif205] quit Step 7 Configure traffic diversion on the core switch. [CSS] ip route-static 1.1.1.1 32 10.3.1.1 //Configure a static route to an address in the NAT address pool of the NGFW and set the next-hop address of the route to the IP address of the upstream VRRP group 1 on the NGFW Module. [CSS] ip route-static 1.1.1.2 32 10.3.1.1 //Configure a static route to an address in the NAT address pool of the NGFW and set the next-hop address of the route to the IP address of the upstream VRRP group 1 on the NGFW Module. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 46 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [CSS] ip route-static 1.1.1.3 32 10.3.1.1 //Configure a static route to the global address of the NAT server configured on the NGFW Module and set the next-hop address of the route to the IP address of the upstream VRRP group 1 on the NGFW Module. [CSS] ip route-static vpn-instance trust 0.0.0.0 0.0.0.0 10.3.2.1 //Configure a default route on the trust virtual switch and set the next hop to the virtual IP address of VRRP group 2. [CSS] ip route-static vpn-instance dmz 0.0.0.0 0.0.0.0 10.3.3.1 //Configure a default route on the dmz virtual switch and set the next hop to the virtual IP address of VRRP group 3. [CSS] ip route-static vpn-instance trust 192.168.2.0 255.255.255.0 vpn-instance dmz 10.1.2.1 //Route from the Trust zone to the DMZ. 10.1.2.1 is the IP address of the VLANIF 205 interface of the access switch. [CSS] ip route-static vpn-instance dmz 192.168.1.0 255.255.255.0 vpn-instance trust 10.1.1.1 //Route from the DMZ to the Trust zone. 10.1.1.1 is the IP address of the VLANIF 204 interface of the access switch. NOTE In the example, NAT is configured on the NGFW Modules. Therefore, configure static routes from the Public virtual switch to the Trust zone and DMZ, and the destination IP addresses in the routes should be post-NAT public IP addresses. If NAT is not configured on the NGFW Modules, the destination IP addresses in the routes must be private IP addresses respectively in the Trust zone and DMZ when you configure static routes from the Public virtual switch to the two zones. In the example, communication packets between the Trust zone and DMZ are not processed by the NGFW Modules. If the enterprise requires that the NGFW Modules process the communication packets between the Trust zone and DMZ, set the next hop to the IP address of the downlink VRRP group on the NGFW Modules when you configure the route for the communications between the Trust zone and DMZ. ----End Verification 1. Run the display hrp state command on NGFW Module_A to check the current HRP status. If the following output is displayed, an HRP relationship is successfully established. HRP_A[Module_A] display hrp state The firewall's config state is: ACTIVE Backup channel usage: 0.01% Time elapsed after the last switchover: 0 days, 0 hours, 1 minutes Current state of virtual routers configured as active: Eth-Trunk1.3 vrid 3 : active (GigabitEthernet1/0/0) : up (GigabitEthernet1/0/1) : up Eth-Trunk1.2 vrid 2 : active (GigabitEthernet1/0/0) : up (GigabitEthernet1/0/1) : up Eth-Trunk1.1 vrid 1 : active (GigabitEthernet1/0/0) : up (GigabitEthernet1/0/1) : up 2. Check whether the access from the intranet to the Internet succeeds and check the session table of each NGFW Module. HRP_A[Module_A] display firewall session table Current Total Sessions : 1 http VPN: public --> public 192.168.1.8:22048[1.1.1.2:2106] --> 3.3.3.3:80 HRP_S[Module_B] display firewall session table Current Total Sessions : 1 http VPN: public --> public Remote 192.168.1.8:22048[1.1.1.2:2106] --> 3.3.3.3:80 According to the preceding output, NGFW Module_A has created a session entry for the access from the intranet to the Internet. A session entry with the Remote tag exists on NGFW Module_B, which indicates that session backup succeeds after you configure hot standby. 3. Issue 34 (2022-10-26) Check whether the access from the Internet to servers in the DMZ succeeds and check the session table of each NGFW Module. Copyright © Huawei Technologies Co., Ltd. 47 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples HRP_A[Module_A] display firewall session table Current Total Sessions : 1 http VPN: public --> public 2.2.2.2:11447 --> 1.1.1.3:8000[192.168.2.8:80] HRP_S[Module_A] display firewall session table Current Total Sessions : 1 http VPN: public --> public Remote 2.2.2.2:11447 --> 1.1.1.3:8000[192.168.2.8:80] 4. Configure a PC in the Trust zone to constantly ping the public address and run the shutdown command on Eth-trunk1 of NGFW Module_A. Then check the status switchover of the NGFW Module and discarded ping packets. If the status switchover is normal, NGFW Module_B becomes the active and carries services. The command prompt of NGFW Module_B is changed from HRP_S to HRP_A, and the command prompt of NGFW Module_A is changed from HRP_A to HRP_S. No or several ping packets (1 to 3 packets, depending on actual network environments) are discarded. Run the undo shutdown command on Eth-trunk1 of NGFW Module_A and check the status switchover of the NGFW Module and discarded ping packets. If the status switchover is normal, NGFW Module_A becomes the active and starts to carry service after the preemption delay (60s by default) expires. The command prompt of NGFW Module_A is changed from HRP_S to HRP_A, and the command prompt of NGFW Module_B is changed from HRP_A to HRP_S. No or several ping packets (1 to 3 packets, depending on actual network environments) are discarded. Configuration Scripts Configuration scripts of the NGFW Modules: Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 48 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples NGFW Module_A NGFW Module_B # sysname Module_A # hrp enable hrp interface Eth-Trunk0 # nat server policy_web protocol tcp global 1.1.1.3 8000 inside 192.168.2.8 www # interface Eth-Trunk0 ip address 10.10.0.1 255.255.255.0 # interface Eth-Trunk1 portswitch port link-type access # interface Eth-Trunk1.1 vlan-type dot1q 201 ip address 10.3.1.2 255.255.255.0 vrrp vrid 1 virtual-ip 10.3.1.1 active # interface Eth-Trunk1.2 vlan-type dot1q 202 ip address 10.3.2.2 255.255.255.0 vrrp vrid 2 virtual-ip 10.3.2.1 active # interface Eth-Trunk1.3 vlan-type dot1q 203 ip address 10.3.3.2 255.255.255.0 vrrp vrid 3 virtual-ip 10.3.3.1 active # interface GigabitEthernet0/0/1 eth-trunk 0 # interface GigabitEthernet0/0/2 eth-trunk 0 # interface GigabitEthernet1/0/0 portswitch port link-type access eth-trunk 1 # interface GigabitEthernet1/0/1 portswitch port link-type access eth-trunk 1 # firewall zone trust set priority 85 add interface Eth-Trunk1.2 # firewall zone untrust set priority 5 add interface Eth-Trunk1.1 # firewall zone dmz set priority 50 add interface Eth-Trunk1.3 # firewall zone hrpzone set priority 65 add interface Eth-Trunk0 # firewall interzone dmz untrust detect ftp # # sysname Module_B # hrp enable hrp standby-device //This command is required only in versions earlier than V100R001C30SPC300. hrp interface Eth-Trunk0 # nat server policy_web protocol tcp global 1.1.1.3 8000 inside 192.168.2.8 www # interface Eth-Trunk0 ip address 10.10.0.2 255.255.255.0 # interface Eth-Trunk1 portswitch port link-type access # interface Eth-Trunk1.1 vlan-type dot1q 201 ip address 10.3.1.3 255.255.255.0 vrrp vrid 1 virtual-ip 10.3.1.1 standby # interface Eth-Trunk1.2 vlan-type dot1q 202 ip address 10.3.2.3 255.255.255.0 vrrp vrid 2 virtual-ip 10.3.2.1 standby # interface Eth-Trunk1.3 vlan-type dot1q 203 ip address 10.3.3.3 255.255.255.0 vrrp vrid 3 virtual-ip 10.3.3.1 standby # interface GigabitEthernet0/0/1 eth-trunk 0 # interface GigabitEthernet0/0/2 eth-trunk 0 # interface GigabitEthernet1/0/0 portswitch port link-type access eth-trunk 1 # interface GigabitEthernet1/0/1 portswitch port link-type access eth-trunk 1 # firewall zone trust set priority 85 add interface Eth-Trunk1.2 # firewall zone untrust set priority 5 add interface Eth-Trunk1.1 # firewall zone dmz set priority 50 add interface Eth-Trunk1.3 # firewall zone hrpzone set priority 65 add interface Eth-Trunk0 # firewall interzone dmz untrust Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 49 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples NGFW Module_A NGFW Module_B ip route-static 0.0.0.0 0.0.0.0 10.3.1.4 ip route-static 1.1.1.1 255.255.255.255 NULL0 ip route-static 1.1.1.2 255.255.255.255 NULL0 ip route-static 1.1.1.3 255.255.255.255 NULL0 ip route-static 192.168.1.0 255.255.255.0 10.3.2.4 ip route-static 192.168.2.0 255.255.255.0 10.3.3.4 # nat address-group addressgroup1 0 section 0 1.1.1.1 1.1.1.2 # security-policy rule name policy_sec1 source-zone trust destination-zone untrust source-address 192.168.1.0 mask 255.255.255.0 action permit rule name policy_sec2 source-zone untrust destination-zone dmz destination-address 192.168.2.0 mask 255.255.255.0 service http service ftp profile ips default action permit # nat-policy rule name policy_nat1 source-zone trust destination-zone untrust source-address 192.168.1.0 mask 255.255.255.0 action nat address-group addressgroup1 # return detect ftp # ip route-static 0.0.0.0 0.0.0.0 10.3.1.4 ip route-static 1.1.1.1 255.255.255.255 NULL0 ip route-static 1.1.1.2 255.255.255.255 NULL0 ip route-static 1.1.1.3 255.255.255.255 NULL0 ip route-static 192.168.1.0 255.255.255.0 10.3.2.4 ip route-static 192.168.2.0 255.255.255.0 10.3.3.4 # nat address-group addressgroup1 0 section 0 1.1.1.1 1.1.1.2 # security-policy rule name policy_sec1 source-zone trust destination-zone untrust source-address 192.168.1.0 mask 255.255.255.0 action permit rule name policy_sec2 source-zone untrust destination-zone dmz destination-address 192.168.2.0 mask 255.255.255.0 service http service ftp profile ips default action permit # nat-policy rule name policy_nat1 source-zone trust destination-zone untrust source-address 192.168.1.0 mask 255.255.255.0 action nat address-group addressgroup1 # return Configuration script of CSS: # ----Traffic diversion configuration---vlan batch 201 to 205 # ip vpn-instance dmz ipv4-family route-distinguisher 200:1 vpn-target 211:1 export-extcommunity vpn-target 211:1 import-extcommunity # ip vpn-instance trust ipv4-family route-distinguisher 100:1 vpn-target 111:1 export-extcommunity vpn-target 111:1 import-extcommunity # interface Vlanif201 ip address 10.3.1.4 255.255.255.0 # interface Vlanif202 ip binding vpn-instance trust ip address 10.3.2.4 255.255.255.0 # interface Vlanif203 ip binding vpn-instance dmz Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 50 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples ip address 10.3.3.4 255.255.255.0 # interface Vlanif204 ip binding vpn-instance trust ip address 10.1.1.2 255.255.255.0 # interface Vlanif205 ip binding vpn-instance dmz ip address 10.1.2.2 255.255.255.0 # interface Eth-Trunk2 description To_TRUST port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 204 # interface Eth-Trunk3 description To_DMZ port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 205 # interface Eth-Trunk5 description To_NGFW_Module_A port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 201 to 205 # interface Eth-Trunk6 description To_NGFW_Module_B port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 201 to 205 # interface XGigabitEthernet1/1/0/0 eth-trunk 5 # interface XGigabitEthernet1/1/0/1 eth-trunk 5 # interface XGigabitEthernet2/1/0/0 eth-trunk 6 # interface XGigabitEthernet2/1/0/1 eth-trunk 6 # ip route-static 1.1.1.1 255.255.255.255 10.3.1.1 ip route-static 1.1.1.2 255.255.255.255 10.3.1.1 ip route-static 1.1.1.3 255.255.255.255 10.3.1.1 ip route-static vpn-instance trust 0.0.0.0 0.0.0.0 10.3.2.1 ip route-static vpn-instance trust 192.168.2.0 255.255.255.0 vpn-instance dmz 10.1.2.1 ip route-static vpn-instance dmz 0.0.0.0 0.0.0.0 10.3.3.1 ip route-static vpn-instance dmz 192.168.1.0 255.255.255.0 vpn-instance trust 10.1.1.1 # return 2.3.3 Layer 3 Active/Standby Hot Standby on the NGFW Modules Installed on a Cluster Switch Where PBR-based Traffic Diversion Is Implemented Service Requirements As shown in Figure 2-10, two switches are deployed in a CSS and two NGFW Modules are installed in slot 1 on the two switches. The two NGFW Modules are Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 51 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples required to implement hot standby and perform security detection on traffic passing through the switches. Two NGFW Modules work in active/standby mode. This example uses NGFW modules running V100R001C30 and switches running V200R008C00. For the configuration examples of NGFW Modules running other versions, see Deployment Guide. Figure 2-10 Networking for Layer-3 dual-NGFW Module deployment and switch CSS NOTE The NGFW Module has two fixed internal Ethernet interfaces: GE1/0/0 to GE1/0/1. The numbering of internal Ethernet interfaces on the switch is determined by the slot in which the NGFW Module is installed. For example, when the NGFW Module is installed in slot 1 on the switch, the internal Ethernet interfaces used by the switch are XGE1/1/0/0 to XGE1/1/0/1. Eth-Trunk2 and Eth-Trunk3 are interfaces of the switches in the CSS. Data Planning Item Data Description Hot standby NGFW Module_A: active - NGFW Module_B: standby NAT Issue 34 (2022-10-26) Source NAT NAT type: PAT Address pool: 1.1.1.1 to 1.1.1.2 The source address is automatically translated for Internet access from a specified private subnet. Copyright © Huawei Technologies Co., Ltd. 52 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Item NAT Server Data Description Global address: 1.1.1.3 A specified server address is translated from a private address to a public address for Internet users to access. Inside address: 192.168.2.8 Securit y policy Policy 1: policy_sec1 Source security zone: Trust Destination security zone: Untrust Users in the Trust zone (residing on 192.168.1.0/24) are allowed to access the Internet. Source IP address: 192.168.1.0 Action: permit Policy 2: policy_sec2 Source security zone: Untrust Destination security zone: DMZ Extranet users are allowed to access the DMZ (residing on 192.168.2.0/24), and intrusion prevention is implemented. Destination IP address: 192.168.2.0 Action: permit Deployment Solution 1. Figure 2-10 can be abstracted as Figure 2-11. You can understand the mapping between the two figures based on interface numbers and actual traffic directions. As shown in Figure 2-11, a default route (next hop: VLANIF201) to the public network, a specific route (next hop: VLANIF202) to the Trust zone, and a specific route (next hop: VLANIF203) to the DMZ need to be configured on the NGFW modules. PBR needs to be configured on the switches to direct traffic to the firewalls. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 53 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Figure 2-11 Configuring VRRP on the NGFW modules and PBR on the switches NOTE Figure 2-11 lists only the switch interfaces involved in the connection with the NGFW Modules. 2. Specify Eth-trunk0 as the heartbeat interface and enable hot standby on each NGFW Module. 3. Configure security functions, such as security policies, nat policies, and IPS on NGFW Module_A. NGFW Module_A will automatically synchronize its configurations to NGFW Module_B. Procedure Step 1 Complete interface and basic network configurations on NGFW Modules. # Configure device name on NGFW Module_A. <sysname> system-view [sysname] sysname Module_A # Configure IP addresses for the interfaces on NGFW Module_A. [Module_A] interface Eth-trunk 1 [Module_A-Eth-Trunk1] quit [Module_A] interface GigabitEthernet 1/0/0 [Module_A-GigabitEthernet1/0/0] Eth-Trunk 1 [Module_A-GigabitEthernet1/0/0] quit [Module_A] interface GigabitEthernet 1/0/1 [Module_A-GigabitEthernet1/0/1] Eth-Trunk 1 [Module_A-GigabitEthernet1/0/1] quit [Module_A] interface Eth-trunk 1.1 [Module_A-Eth-Trunk1.1] ip address 10.3.1.2 24 [Module_A-Eth-Trunk1.1] vlan-type dot1q 201 [Module_A-Eth-Trunk1.1] quit [Module_A] interface Eth-trunk 1.2 Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 54 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [Module_A-Eth-Trunk1.2] ip address 10.3.2.2 24 [Module_A-Eth-Trunk1.2] vlan-type dot1q 202 [Module_A-Eth-Trunk1.2] quit [Module_A] interface Eth-trunk 1.3 [Module_A-Eth-Trunk1.3] ip address 10.3.3.2 24 [Module_A-Eth-Trunk1.3] vlan-type dot1q 203 [Module_A-Eth-Trunk1.3] quit [Module_A] interface Eth-Trunk 0 [Module_A-Eth-Trunk0] ip address 10.10.0.1 24 [Module_A-Eth-Trunk0] quit [Module_A] interface GigabitEthernet 0/0/1 [Module_A-GigabitEthernet0/0/1] Eth-Trunk 0 [Module_A-GigabitEthernet0/0/1] quit [Module_A] interface GigabitEthernet 0/0/2 [Module_A-GigabitEthernet0/0/2] Eth-Trunk 0 [Module_A-GigabitEthernet0/0/2] quit # Assign the interfaces of NGFW Module_A to security zones. [Module_A] firewall zone untrust [Module_A-zone-untrust] add interface Eth-trunk 1.1 [Module_A-zone-untrust] quit [Module_A] firewall zone trust [Module_A-zone-trust] add interface Eth-trunk 1.2 [Module_A-zone-trust] quit [Module_A] firewall zone dmz [Module_A-zone-dmz] add interface Eth-trunk 1.3 [Module_A-zone-dmz] quit [Module_A] firewall zone name hrpzone [Module_A-zone-hrpzone] set priority 65 [Module_A-zone-hrpzone] add interface Eth-Trunk 0 [Module_A-zone-hrpzone] quit # Configure device name on NGFW Module_B. <sysname> system-view [sysname] sysname Module_B # Configure IP addresses for the interfaces on NGFW Module_B. [Module_B] interface Eth-trunk 1 [Module_B-Eth-Trunk1] quit [Module_B] interface GigabitEthernet 1/0/0 [Module_B-GigabitEthernet1/0/0] Eth-Trunk 1 [Module_B-GigabitEthernet1/0/0] quit [Module_B] interface GigabitEthernet 1/0/1 [Module_B-GigabitEthernet1/0/1] Eth-Trunk 1 [Module_B-GigabitEthernet1/0/1] quit [Module_B] interface Eth-trunk 1.1 [Module_B-Eth-Trunk1.1] ip address 10.3.1.3 24 [Module_B-Eth-Trunk1.1] vlan-type dot1q 201 [Module_B-Eth-Trunk1.1] quit [Module_B] interface Eth-trunk 1.2 [Module_B-Eth-Trunk1.2] ip address 10.3.2.3 24 [Module_B-Eth-Trunk1.2] vlan-type dot1q 202 [Module_B-Eth-Trunk1.2] quit [Module_B] interface Eth-trunk 1.3 [Module_B-Eth-Trunk1.3] ip address 10.3.3.3 24 [Module_B-Eth-Trunk1.3] vlan-type dot1q 203 [Module_B-Eth-Trunk1.3] quit [Module_B] interface Eth-Trunk 0 [Module_B-Eth-Trunk0] ip address 10.10.0.2 24 [Module_B-Eth-Trunk0] quit [Module_B] interface GigabitEthernet 0/0/1 [Module_B-GigabitEthernet0/0/1] Eth-Trunk 0 [Module_B-GigabitEthernet0/0/1] quit [Module_B] interface GigabitEthernet 0/0/2 [Module_B-GigabitEthernet0/0/2] Eth-Trunk 0 [Module_B-GigabitEthernet0/0/2] quit # Assign the interfaces of NGFW Module_B to security zones. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 55 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [Module_B] firewall zone untrust [Module_B-zone-untrust] add interface Eth-trunk 1.1 [Module_B-zone-untrust] quit [Module_B] firewall zone trust [Module_B-zone-trust] add interface Eth-trunk 1.2 [Module_B-zone-trust] quit [Module_B] firewall zone dmz [Module_B-zone-dmz] add interface Eth-trunk 1.3 [Module_B-zone-dmz] quit [Module_B] firewall zone name hrpzone [Module_B-zone-hrpzone] set priority 65 [Module_B-zone-hrpzone] add interface Eth-Trunk 0 [Module_B-zone-hrpzone] quit Step 2 Create static routes on NGFW Modules. # On NGFW Module_A, configure an upstream static route (default route) with the next-hop address set to the IP address of VLANIF201. [Module_A] ip route-static 0.0.0.0 0.0.0.0 10.3.1.4 # On NGFW Module_A, configure a downstream static route to the Trust zone, with the destination address being the address of the Trust zone and next-hop address being the address of VLANIF202 on the connected switch. [Module_A] ip route-static 192.168.1.0 255.255.255.0 10.3.2.4 # On NGFW Module_A, configure a downstream static route to the DMZ, with the destination address being the address of the DMZ and next-hop address being the address of VLANIF203 on the connected switch. [Module_A] ip route-static 192.168.2.0 255.255.255.0 10.3.3.4 # On NGFW Module_A, configure a black-hole route to an address in the source NAT address pool to prevent routing loops. In this example, the address range is 1.1.1.1-1.1.1.2 in the source NAT address pool. [Module_A] ip route-static 1.1.1.1 255.255.255.255 null 0 [Module_A] ip route-static 1.1.1.2 255.255.255.255 null 0 # On NGFW Module_A, configure a black-hole route to the global address of the NAT server to prevent routing loops. In this example, the global address of the NAT server is 1.1.1.3. [Module_A] ip route-static 1.1.1.3 255.255.255.255 null 0 # On NGFW Module_B, configure an upstream static route (default route) with the next-hop address set to the IP address of VLANIF201 on the connected switch. [Module_B] ip route-static 0.0.0.0 0.0.0.0 10.3.1.4 # On NGFW Module_B, configure a downstream static route to the Trust zone, with the destination address being the address of the Trust zone and next-hop address being the address of VLANIF202 on the connected switch. [Module_B] ip route-static 192.168.1.0 255.255.255.0 10.3.2.4 # On NGFW Module_B, configure a downstream static route to the DMZ, with the destination address being the address of the DMZ and next-hop address being the address of VLANIF203 on the connected switch. [Module_B] ip route-static 192.168.2.0 255.255.255.0 10.3.3.4 # On NGFW Module_B, configure a black-hole route to an address in the source NAT address pool to prevent routing loops. In this example, the address range is 1.1.1.1-1.1.1.2 in the source NAT address pool. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 56 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [Module_B] ip route-static 1.1.1.1 255.255.255.255 null 0 [Module_B] ip route-static 1.1.1.2 255.255.255.255 null 0 # On NGFW Module_B, configure a black-hole route to the global address of the NAT server to prevent routing loops. In this example, the global address of the NAT server is 1.1.1.3. [Module_B] ip route-static 1.1.1.3 255.255.255.255 null 0 Step 3 Configure hot standby on NGFW Modules. # Configure VRRP groups on NGFW Module_A. [Module_A] interface Eth-trunk1.1 [Module_A-Eth-Trunk1.1] vrrp vrid 1 virtual-ip 10.3.1.1 active [Module_A-Eth-Trunk1.1] quit [Module_A] interface Eth-trunk1.2 [Module_A-Eth-Trunk1.2] vrrp vrid 2 virtual-ip 10.3.2.1 active [Module_A-Eth-Trunk1.2] quit [Module_A] interface Eth-trunk1.3 [Module_A-Eth-Trunk1.3] vrrp vrid 3 virtual-ip 10.3.3.1 active [Module_A-Eth-Trunk1.3] quit # Specify the heartbeat interface and enable hot standby on NGFW Module_A. [Module_A] hrp interface Eth-Trunk 0 [Module_A] hrp enable # Configure VRRP groups on NGFW Module_B. [Module_B] interface Eth-trunk1.1 [Module_B-Eth-Trunk1.1] vrrp vrid 1 virtual-ip 10.3.1.1 standby [Module_B-Eth-Trunk1.1] quit [Module_B] interface Eth-trunk1.2 [Module_B-Eth-Trunk1.2] vrrp vrid 2 virtual-ip 10.3.2.1 standby [Module_B-Eth-Trunk1.2] quit [Module_B] interface Eth-trunk1.3 [Module_B-Eth-Trunk1.3] vrrp vrid 3 virtual-ip 10.3.3.1 standby [Module_B-Eth-Trunk1.3] quit # Specify the heartbeat interface and enable hot standby on NGFW Module_B. [Module_B] hrp interface Eth-Trunk 0 [Module_B] hrp enable [Module_B] hrp standby-device //This command is required only in versions earlier than V100R001C30SPC300. NOTE After hot standby is configured, the configurations and sessions on the active device are synchronized to the standby device; therefore, you only need to perform the following configurations on the active NGFW Module_A. Before configuring intrusion prevention, ensure that the required license is loaded and the intrusion prevention signature database is the latest version. When configuring intrusion prevention, use the default intrusion prevention profile default. Step 4 Configure security services on NGFW Modules. # On NGFW Module_A, configure a security policy to allow users in the Trust zone (network segment 192.168.1.0/24) to access the Internet. HRP_A[Module_A] security-policy HRP_A[Module_A-policy-security] rule name policy_sec1 HRP_A[Module_A-policy-security-rule-policy_sec1] source-zone trust HRP_A[Module_A-policy-security-rule-policy_sec1] destination-zone untrust HRP_A[Module_A-policy-security-rule-policy-sec1] source-address 192.168.1.0 24 HRP_A[Module_A-policy-security-rule-policy_sec1] action permit HRP_A[Module_A-policy-security-rule-policy_sec1] quit Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 57 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples # On NGFW Module_A, configure a security policy to allow extranet users to access the DMZ (network segment 192.168.2.0/24) and configure intrusion prevention. HRP_A[Module_A-policy-security] rule name policy_sec2 HRP_A[Module_A-policy-security-rule-policy_sec2] source-zone untrust HRP_A[Module_A-policy-security-rule-policy_sec2] destination-zone dmz HRP_A[Module_A-policy-security-rule-policy-sec2] destination-address 192.168.2.0 24 HRP_A[Module_A-policy-security-rule-policy_sec2] service http ftp HRP_A[Module_A-policy-security-rule-policy_sec2] profile ips default HRP_A[Module_A-policy-security-rule-policy_sec2] action permit HRP_A[Module_A-policy-security-rule-policy_sec2] quit HRP_A[Module_A-policy-security] quit # Configure ASPF on NGFW Module_A. FTP is used as an example. HRP_A[Module_A] firewall interzone untrust dmz HRP_A[Module_A-interzone-dmz-untrust] detect ftp HRP_A[Module_A-interzone-dmz-untrust] quit # Configure a NAT address pool. HRP_A[Module_A] nat address-group addressgroup1 HRP_A[Module_A-address-group-addressgroup1] section 0 1.1.1.1 1.1.1.2 HRP_A[Module_A-address-group-addressgroup1] quit # Configure a source NAT policy for Internet access from the specified private subnet. HRP_A[Module_A] nat-policy HRP_A[Module_A-policy-nat] rule name policy_nat1 HRP_A[Module_A-policy-nat-rule-policy_nat1] source-zone trust HRP_A[Module_A-policy-nat-rule-policy_nat1] destination-zone untrust HRP_A[Module_A-policy-nat-rule-policy_nat1] source-address 192.168.1.0 24 HRP_A[Module_A-policy-nat-rule-policy_nat1] action nat address-group addressgroup1 HRP_A[Module_A-policy-nat-rule-policy_nat1] quit HRP_A[Module_A-policy-nat] quit # Configure the NAT server function to translate the private address of a specific server in the DMZ into a public address for user access. In this example, private address 192.168.2.8:80 of the web server in the DMZ is translated into public address 1.1.1.3:8000. HRP_A[Module_A] nat server policy_web protocol tcp global 1.1.1.3 8000 inside 192.168.2.8 80 # Save configurations on NGFW Module_A and NGFW Module_B. HRP_A<Module_A> save The current configurations will be written to the device. Are you sure?[Y/N] y Now saving the current configuration to the device...... Info:The Current Configuration was saved to the device successfully HRP_S<Module_B> save The current configurations will be written to the device. Are you sure?[Y/N] y Now saving the current configuration to the device...... Info:The Current Configuration was saved to the device successfully Step 5 Configure the core switches to form a CSS. 1. Install the hardware and connect the cables. For details, see the CSS Installation Guide. 2. Set the CSS connection mode (such as the CSS card connection mode), CSS ID, and CSS priority. # Configure the CSS on SwitchA. In the example, the CSS connection mode is CSS card connection mode, the CSS ID is 1, and the CSS priority is 100. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 58 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples <Huawei> system-view [Huawei] sysname SwitchA [SwitchA] set css mode css-card card connection mode. [SwitchA] set css id 1 [SwitchA] set css priority 100 //Set the CSS connection mode. The default mode is CSS //Set the CSS ID. The default value is 1. //Set the CSS priority. The default value is 1. # Configure the CSS on SwitchB. In the example, the CSS connection mode is CSS card connection mode, the CSS ID is 2, and the CSS priority is 10. <Huawei> system-view [Huawei] sysname SwitchB [SwitchB] set css mode css-card [SwitchB] set css id 2 [SwitchB] set css priority 10 3. Enable the CSS function. # To use SwitchA as the active switch, enable CSS on SwitchA and then restart SwitchA. [SwitchA] css enable Warning: The CSS configuration will take effect only after the system is rebooted. T he next CSS mode is CSS card. Reboot now? [Y/N]:y # Enable CSS on SwitchB and then restart SwitchB. [SwitchB] css enable Warning: The CSS configuration will take effect only after the system is rebooted. T he next CSS mode is CSS card. Reboot now? [Y/N]:y 4. Check whether the CSS is established. # Log in to the CSS from the console port of any MPU and run the following command to view the CSS status. <SwitchA> display css status CSS Enable switch On Chassis Id CSS Enable CSS Status CSS Mode Priority Master Force -----------------------------------------------------------------------------Off 1 On Master CSS card 100 2 On Standby CSS card 10 Off If the CSS IDs, CSS priorities, CSS enabling status, and CSS status of the two member switches are displayed, as shown in the preceding information, the CSS has been established. You are advised to configure MAD to minimize the impact of a CSS split on services. Detailed configurations will not be described here. 5. Rename the cluster system to CSS. <SwitchA> system-view [SwitchA] sysname CSS [CSS] Step 6 Configure interfaces and VLANs for switches. This example describes how to configure interoperation between the switch and NGFW modules. [CSS] vlan batch 201 to 203 //Create VLANs. [CSS] interface eth-trunk 5 [CSS-Eth-Trunk5] description To_NGFW_Module_A [CSS-Eth-Trunk5] trunkport xgigabitethernet 1/1/0/0 to 1/1/0/1 //Create Eth-Trunk5 on the CSS and add internal Ethernet interfaces to Eth-Trunk5. [CSS-Eth-Trunk5] port link-type trunk [CSS-Eth-Trunk5] undo port trunk allow-pass vlan 1 [CSS-Eth-Trunk5] port trunk allow-pass vlan 201 to 203 //Configure Eth-Trunk5 to permit traffic from VLANs 201, 202, and 203. [CSS-Eth-Trunk5] quit Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 59 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [CSS] interface eth-trunk 6 [CSS-Eth-Trunk6] description To_NGFW_Module_B [CSS-Eth-Trunk6] trunkport xgigabitethernet 2/1/0/0 to 2/1/0/1 //Create Eth-Trunk6 on the CSS and add internal Ethernet interfaces to Eth-Trunk6. [CSS-Eth-Trunk6] port link-type trunk [CSS-Eth-Trunk6] undo port trunk allow-pass vlan 1 [CSS-Eth-Trunk6] port trunk allow-pass vlan 201 to 203 //Configure Eth-Trunk6 to permit traffic from VLANs 201, 202, and 203. [CSS-Eth-Trunk6] quit [CSS] interface vlanif 201 [CSS-Vlanif201] ip address 10.3.1.4 24 //Configure an IP address for VLANIF201. [CSS-Vlanif201] quit [CSS] interface vlanif 202 [CSS-Vlanif202] ip address 10.3.2.4 24 //Configure an IP address for VLANIF202. [CSS-Vlanif202] quit [CSS] interface vlanif 203 [CSS-Vlanif203] ip address 10.3.3.4 24 //Configure an IP address for VLANIF203. [CSS-Vlanif203] quit Step 7 Configure traffic diversion on the switch. This example describes how to configure interoperation between the switch and NGFW modules. [CSS] acl 3001 //Create ACL3001. [CSS-acl-adv-3001] rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255 // Configure a rule for ACL3001: source network segment 192.168.1.0 and destination network segment 192.168.2.0. [CSS-acl-adv-3001] rule 10 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 // Configure a rule for ACL3001: source network segment 192.168.2.0 and destination network segment 192.168.1.0. [CSS-acl-adv-3001] quit [CSS] traffic classifier c1 precedence 5 //Create traffic classifier c1. [CSS-classifier-c1] if-match acl 3001 //Match packets exchanged between the Trust zone and DMZ with the ACL3001 rule. [CSS-classifier-c1] quit [CSS] traffic behavior b1 //Create traffic behavior b1. [CSS-behavior-b1] permit //Permit the matching packets. [CSS-behavior-b1] quit [CSS] acl 3002 //Create ACL3002. [CSS-acl-adv-3002] rule 5 permit ip source 192.168.1.0 0.0.0.255 //Configure a rule for ACL3002: source network segment 192.168.1.0. [CSS-acl-adv-3002] quit [CSS] traffic classifier c2 precedence 10 //Create traffic classifier c2. [CSS-classifier-c2] if-match acl 3002 //Match the packets from network segment 192.168.1.0, namely, packets from the Trust zone to the Internet, with ACL3002. [CSS-classifier-c2] quit [CSS] traffic behavior b2 //Create traffic behavior b2. [CSS-behavior-b2] redirect ip-nexthop 10.3.2.1 //Redirect the matching packets to address 10.3.2.1, namely, the connected NGFW Module. [CSS-behavior-b2] quit [CSS] traffic policy p1 //Create traffic policy p1. [CSS-trafficpolicy-p1] classifier c1 behavior b1 //Bind traffic classifier c1 and traffic behavior b1 with traffic policy p1. All packets exchanged between the Trust zone and DMZ are directly forwarded by the switch, without being forwarded to the NGFW Module. [CSS-trafficpolicy-p1] classifier c2 behavior b2 //Bind traffic classifier c2 and traffic behavior b2 with traffic policy p1. All packets from the Trust zone to the Internet are redirected to the NGFW Module. [CSS-trafficpolicy-p1] quit [CSS] interface eth-trunk 2 //Access the interface connecting the switch to the Trust zone. [CSS-Eth-Trunk2] traffic-policy p1 inbound //Apply traffic policy P1 in the inbound direction of the interface connecting the switch to the Trust zone. [CSS-Eth-Trunk2] quit [CSS] acl 3003 //Create ACL3003. [CSS-acl-adv-3003] rule 5 permit ip source 192.168.2.0 0.0.0.255 //Configure a rule for ACL3003: source network segment 192.168.2.0. [CSS-acl-adv-3003] quit [CSS] traffic classifier c3 precedence 15 //Create traffic classifier c3. [CSS-classifier-c3] if-match acl 3003 //Match all packets from network segment 192.168.2.0, namely, all packets from the DMZ to the Internet, with the ACL3003 rule. [CSS-classifier-c3] quit [CSS] traffic behavior b3 //Create traffic behavior b3. [CSS-behavior-b3] redirect ip-nexthop 10.3.3.1 //Redirect the matching packets to address 10.3.3.1, Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 60 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples namely the NGFW Module. [CSS-behavior-b3] quit [CSS] traffic policy p3 //Create traffic policy p3. [CSS-trafficpolicy-p3] classifier c1 behavior b1 //Bind traffic classifier c1 and traffic behavior b1 with traffic policy p3. All packets exchanged between the Trust zone and DMZ are directly forwarded by the switch, without being forwarded to the NGFW Module. [CSS-trafficpolicy-p3] classifier c3 behavior b3 //Bind traffic classifier c3 and traffic behavior b3 with traffic policy p3. All traffic from the DMZ to the Internet are directed to the NGFW Module. [CSS-trafficpolicy-p3] quit [CSS] interface eth-trunk 3 //Access the view of the interface connecting the switch to the Trust zone. [CSS-Eth-Trunk3] traffic-policy p3 inbound //Apply traffic policy p3 in the inbound direction of the interface connecting the switch to the DMZ. [CSS-Eth-Trunk3] quit [CSS] ip route-static 1.1.1.1 32 10.3.1.1 //Configure a static route to an address in the NAT address pool of the NGFW and set the next-hop address of the route to the IP address of the upstream VRRP group on the NGFW Module. [CSS] ip route-static 1.1.1.2 32 10.3.1.1 //Configure a static route to an address in the NAT address pool of the NGFW and set the next-hop address of the route to the IP address of the upstream VRRP group on the NGFW Module. [CSS] ip route-static 1.1.1.3 32 10.3.1.1 //Configure a static route to the global address of the NAT server configured on the NGFW Module and set the next-hop address of the route to the IP address of the upstream VRRP group on the NGFW Module. NOTE In this example, the source NAT and NAT server functions are configured on the NGFW Module. For the switch, the destination address of traffic sent from the public network the private network is a post-NAT address. Therefore, you can configure a static route on the switch to direct the traffic sent from the public address to the private network to the NGFW Module. If no source NAT or NAT server function is configured on the NGFW Module, for the switch, the destination address of traffic sent from the public network to the private network is still a private network. In this case, you need to configure a traffic policy on the upstream interface of the switch to direct the traffic to the NGFW Module. [CSS] acl 3004 //Create ACL3004. [CSS-acl-adv-3004] rule 5 permit ip destination 192.168.1.0 0.0.0.255 //Configure a rule for ACL3004: destination network segment 192.168.1.0. [CSS-acl-adv-3004] rule 10 permit ip destination 192.168.2.0 0.0.0.255 //Configure a rule for ACL3004: destination network segment 192.168.2.0. [CSS-acl-adv-3004] quit [CSS] traffic classifier c4 precedence 20 //Create traffic classifier c4. [CSS-classifier-c4] if-match acl 3004 //Match the packets whose destination network segments are 192.168.1.0 and 192.168.2.0, namely, all packets from the Internet to the intranet, with the ACL3004 rule. [CSS-classifier-c4] quit [CSS] traffic behavior b4 //Create traffic behavior b4. [CSS-behavior-b4] redirect ip-nexthop 10.3.1.1 //Redirect the matching packets to address 10.3.1.1, namely, the NGFW Module. [CSS-behavior-b4] quit [CSS] traffic policy p4 //Create traffic policy p4. [CSS-trafficpolicy-p4] classifier c4 behavior b4 precedence 20 //Bind traffic classifier c4 and traffic behavior b4 with traffic policy p4. All traffic from the Internet to the intranet is directed to the NGFW Module. [CSS-trafficpolicy-p4] quit [CSS] interface eth-trunk 4 //Access the view of the interface connecting the switch to the Internet. [CSS-Eth-Trunk4] traffic-policy p4 inbound //Apply traffic policy p4 in the inbound direction of the interface connecting the switch to the Internet. [CSS-Eth-Trunk4] quit ----End Verification 1. Run the display hrp state command on NGFW Module_A to check the current HRP status. If the following output is displayed, an HRP relationship is successfully established. HRP_A[Module_A] display hrp state The firewall's config state is: ACTIVE Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 61 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Backup channel usage: 0.01% Time elapsed after the last switchover: 0 days, 0 hours, 1 minutes Current state of virtual routers configured as active: Eth-Trunk1.3 vrid 3 : active (GigabitEthernet1/0/0) : up (GigabitEthernet1/0/1) : up Eth-Trunk1.2 vrid 2 : active (GigabitEthernet1/0/0) : up (GigabitEthernet1/0/1) : up Eth-Trunk1.1 vrid 1 : active (GigabitEthernet1/0/0) : up (GigabitEthernet1/0/1) : up 2. Check whether the access from the intranet to the Internet succeeds and check the session table of each NGFW Module. HRP_A[Module_A] display firewall session table Current Total Sessions : 1 http VPN: public --> public 192.168.1.8:22048[1.1.1.1:2106] --> 3.3.3.3:80 HRP_S[Module_B] display firewall session table Current Total Sessions : 1 http VPN: public --> public Remote 192.168.1.8:22048[1.1.1.1:2106] --> 3.3.3.3:80 According to the preceding output, NGFW Module_A has created a session entry for the access from the intranet to the Internet. A session entry with the Remote tag exists on NGFW Module_B, which indicates that session backup succeeds after you configure hot standby. 3. Check whether the access from the Internet to servers in the DMZ succeeds and check the session table of each NGFW Module. HRP_A[Module_A] display firewall session table Current Total Sessions : 1 http VPN: public --> public 2.2.2.2:11447 --> 1.1.1.3:8000[192.168.2.8:80] HRP_S[Module_A] display firewall session table Current Total Sessions : 1 http VPN: public --> public Remote 2.2.2.2:11447 --> 1.1.1.3:8000[192.168.2.8:80] 4. Configure a PC in the Trust zone to constantly ping the public address and run the shutdown command on Eth-trunk1 of NGFW Module_A. Then check the status switchover of the NGFW Module and discarded ping packets. If the status switchover is normal, NGFW Module_B becomes the active and carries services. The command prompt of NGFW Module_B is changed from HRP_S to HRP_A, and the command prompt of NGFW Module_A is changed from HRP_A to HRP_S. No or several ping packets (1 to 3 packets, depending on actual network environments) are discarded. Run the undo shutdown command on Eth-trunk1 of NGFW Module_A and check the status switchover of the NGFW Module and discarded ping packets. If the status switchover is normal, NGFW Module_A becomes the active and starts to carry service after the preemption delay (60s by default) expires. The command prompt of NGFW Module_A is changed from HRP_S to HRP_A, and the command prompt of NGFW Module_B is changed from HRP_A to HRP_S. No or several ping packets (1 to 3 packets, depending on actual network environments) are discarded. Configuration Scripts Configuration scripts of the NGFW Modules: Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 62 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples NGFW Module_A NGFW Module_B # sysname Module_A # hrp enable hrp interface Eth-Trunk0 # nat server policy_web protocol tcp global 1.1.1.3 8000 inside 192.168.2.8 www # interface Eth-Trunk0 ip address 10.10.0.1 255.255.255.0 # interface Eth-Trunk1 portswitch port link-type access # interface Eth-Trunk1.1 vlan-type dot1q 201 ip address 10.3.1.2 255.255.255.0 vrrp vrid 1 virtual-ip 10.3.1.1 active # interface Eth-Trunk1.2 vlan-type dot1q 202 ip address 10.3.2.2 255.255.255.0 vrrp vrid 2 virtual-ip 10.3.2.1 active # interface Eth-Trunk1.3 vlan-type dot1q 203 ip address 10.3.3.2 255.255.255.0 vrrp vrid 3 virtual-ip 10.3.3.1 active # interface GigabitEthernet0/0/1 eth-trunk 0 # interface GigabitEthernet0/0/2 eth-trunk 0 # interface GigabitEthernet1/0/0 portswitch port link-type access eth-trunk 1 # interface GigabitEthernet1/0/1 portswitch port link-type access eth-trunk 1 # firewall zone trust set priority 85 add interface Eth-Trunk1.2 # firewall zone untrust set priority 5 add interface Eth-Trunk1.1 # firewall zone dmz set priority 50 add interface Eth-Trunk1.3 # firewall zone hrpzone set priority 65 add interface Eth-Trunk0 # firewall interzone dmz untrust detect ftp # # sysname Module_B # hrp enable hrp interface Eth-Trunk0 hrp standby-device //This command is required only in versions earlier than V100R001C30SPC300. # nat server policy_web protocol tcp global 1.1.1.3 8000 inside 192.168.2.8 www # interface Eth-Trunk0 ip address 10.10.0.2 255.255.255.0 # interface Eth-Trunk1 portswitch port link-type access # interface Eth-Trunk1.1 vlan-type dot1q 201 ip address 10.3.1.3 255.255.255.0 vrrp vrid 1 virtual-ip 10.3.1.1 standby # interface Eth-Trunk1.2 vlan-type dot1q 202 ip address 10.3.2.3 255.255.255.0 vrrp vrid 2 virtual-ip 10.3.2.1 standby # interface Eth-Trunk1.3 vlan-type dot1q 203 ip address 10.3.3.3 255.255.255.0 vrrp vrid 3 virtual-ip 10.3.3.1 standby # interface GigabitEthernet0/0/1 eth-trunk 0 # interface GigabitEthernet0/0/2 eth-trunk 0 # interface GigabitEthernet1/0/0 portswitch port link-type access eth-trunk 1 # interface GigabitEthernet1/0/1 portswitch port link-type access eth-trunk 1 # firewall zone trust set priority 85 add interface Eth-Trunk1.2 # firewall zone untrust set priority 5 add interface Eth-Trunk1.1 # firewall zone dmz set priority 50 add interface Eth-Trunk1.3 # firewall zone hrpzone set priority 65 add interface Eth-Trunk0 # firewall interzone dmz untrust Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 63 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples NGFW Module_A NGFW Module_B ip route-static 0.0.0.0 0.0.0.0 10.3.1.4 ip route-static 1.1.1.1 255.255.255.255 NULL0 ip route-static 1.1.1.2 255.255.255.255 NULL0 ip route-static 1.1.1.3 255.255.255.255 NULL0 ip route-static 192.168.1.0 255.255.255.0 10.3.2.4 ip route-static 192.168.2.0 255.255.255.0 10.3.3.4 # nat address-group addressgroup1 0 section 0 1.1.1.1 1.1.1.2 # security-policy rule name policy_sec1 source-zone trust destination-zone untrust source-address 192.168.1.0 mask 255.255.255.0 action permit rule name policy_sec2 source-zone untrust destination-zone dmz destination-address 192.168.2.0 mask 255.255.255.0 service http service ftp profile ips default action permit # nat-policy rule name policy_nat1 source-zone trust destination-zone untrust source-address 192.168.1.0 mask 255.255.255.0 action nat address-group addressgroup1 # return detect ftp # ip route-static 0.0.0.0 0.0.0.0 10.3.1.4 ip route-static 1.1.1.1 255.255.255.255 NULL0 ip route-static 1.1.1.2 255.255.255.255 NULL0 ip route-static 1.1.1.3 255.255.255.255 NULL0 ip route-static 192.168.1.0 255.255.255.0 10.3.2.4 ip route-static 192.168.2.0 255.255.255.0 10.3.3.4 # nat address-group addressgroup1 0 section 0 1.1.1.1 1.1.1.2 # security-policy rule name policy_sec1 source-zone trust destination-zone untrust source-address 192.168.1.0 mask 255.255.255.0 action permit rule name policy_sec2 source-zone untrust destination-zone dmz destination-address 192.168.2.0 mask 255.255.255.0 service http service ftp profile ips default action permit # nat-policy rule name policy_nat1 source-zone trust destination-zone untrust source-address 192.168.1.0 mask 255.255.255.0 action nat address-group addressgroup1 # return Configuration script of CSS: # ----Traffic diversion configuration---vlan batch 201 to 203 # acl number 3001 rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255 rule 10 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 acl number 3002 rule 5 permit ip source 192.168.1.0 0.0.0.255 acl number 3003 rule 5 permit ip source 192.168.2.0 0.0.0.255 acl number 3004 rule 5 permit destination 192.168.1.0 0.0.0.255 rule 10 permit destination 192.168.2.0 0.0.0.255 # traffic classifier c1 operator or precedence 5 if-match acl 3001 traffic classifier c2 operator or precedence 10 if-match acl 3002 traffic classifier c3 operator or precedence 15 if-match acl 3003 traffic classifier c4 operator or precedence 20 if-match acl 3004 # traffic behavior b1 permit Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 64 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples traffic behavior b2 permit redirect ip-nexthop 10.3.2.1 traffic behavior b3 permit redirect ip-nexthop 10.3.3.1 traffic behavior b4 permit redirect ip-nexthop 10.3.1.1 # traffic policy p1 match-order config classifier c1 behavior b1 classifier c2 behavior b2 traffic policy p3 match-order config classifier c1 behavior b1 classifier c3 behavior b3 traffic policy p4 match-order config classifier c4 behavior b4 # interface Vlanif201 ip address 10.3.1.4 255.255.255.0 # interface Vlanif202 ip address 10.3.2.4 255.255.255.0 # interface Vlanif203 ip address 10.3.3.4 255.255.255.0 # interface Eth-Trunk2 traffic-policy p1 inbound # interface Eth-Trunk3 traffic-policy p3 inbound # interface Eth-Trunk4 traffic-policy p4 inbound # interface Eth-Trunk5 description To_NGFW_Module_A port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 201 to 203 # interface Eth-Trunk6 description To_NGFW_Module_B port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 201 to 203 # interface XGigabitEthernet1/1/0/0 eth-trunk 5 # interface XGigabitEthernet1/1/0/1 eth-trunk 5 # interface XGigabitEthernet2/1/0/0 eth-trunk 6 # interface XGigabitEthernet2/1/0/1 eth-trunk 6 # ip route-static 1.1.1.1 255.255.255.255 10.3.1.1 ip route-static 1.1.1.2 255.255.255.255 10.3.1.1 ip route-static 1.1.1.3 255.255.255.255 10.3.1.1 # return Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 65 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples 2.3.4 Layer 3 Active/Standby Hot Standby on the NGFW Modules Installed on a Cluster Switch Where VLAN-based Traffic Diversion Is Implemented Service Requirements As shown in Figure 2-12, two switches form a CSS, and two NGFW Modules are installed in slot 1 of the switches respective and implement hot standby. The NGFW modules implement security check on traffic sent by intranet users to access the server area or the Internet. This example uses NGFW modules running V100R001C30 and switches running V200R008C00. For the configuration examples of NGFW Modules running other versions, see Deployment Guide. Figure 2-12 Switch CSS and NGFW Module hot standby networking NOTE The NGFW Module has two fixed internal Ethernet interfaces: GE1/0/0 to GE1/0/1. The numbering of internal Ethernet interfaces on the switch is determined by the slot in which the NGFW Module is installed. For example, when the NGFW Module is installed in slot 1 on the switch, the internal Ethernet interfaces used by the switch are XGE1/1/0/0 to XGE1/1/0/1. Eth-Trunk2 and Eth-Trunk3 are interfaces of the switches in the CSS. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 66 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Deployment Solution The NGFW Modules work at Layer 3, and the upstream and downstream network gateways point to the NGFW Modules. The switches work at Layer 2. 1. The interfaces connecting each NGFW Module and switch are bundled into an Eth-Trunk interface. The Eth-Trunk interface is Eth-Trunk 1 on each NGFW Module, Eth-Trunk 10 on the SwitchA, and Eth-Trunk 11 on the SwitchB. 2. The Eth-Trunk at the switch side is configured to work in Trunk mode and allows packets from VLANs 301, 302, and 200 to pass. Configure three EthTrunk subinterfaces at the NGFW Module side to carry out dot1q termination for packets from VLANs 301, 302, and 200 respectively and perform Layer-3 forwarding. 3. Two NGFW modules form hot standby in active/standby mode. Therefore, a VRRP group needs to be configured on the upstream and downstream subinterfaces of each NGFW Module. One NGFW Module is added to an active VGMP group, and the other NGFW Module is added to a standby VGMP group. The virtual gateway IP addresses of the VRRP group are the gateway addresses of the downstream and upstream networks. Figure 2-13 provides logical networking. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 67 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Figure 2-13 Configuring Eth-Trunk subinterfaces and VRRP on the NGFW Modules NOTE Figure 2-13 provides information only interfaces related to the switches and NGFW Modules. 4. Bundle GE0/0/1 and GE0/0/2 interfaces on the panel of each NGFW Module into an Eth-Trunk0 interface, which functions as the heartbeat interface and backup channel and enable hot standby. 5. Configure security functions, such as security policies and IPS on NGFW Module_A. NGFW Module_A will automatically synchronize its configurations to NGFW Module_B. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 68 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples Procedure Step 1 Complete interface and basic network configurations on NGFW Modules. # Configure device name on NGFW Module_A. <sysname> system-view [sysname] sysname Module_A # Add the interfaces connecting NGFW Module_A to its connected switch to EthTrunk 1. [Module_A] interface Eth-Trunk 1 [Module_A-Eth-Trunk1] description To_SWITCHA_trunk10 [Module_A-Eth-Trunk1] quit [Module_A] interface GigabitEthernet 1/0/0 [Module_A-GigabitEthernet1/0/0] Eth-Trunk 1 [Module_A-GigabitEthernet1/0/0] quit [Module_A] interface GigabitEthernet 1/0/1 [Module_A-GigabitEthernet1/0/1] Eth-Trunk 1 [Module_A-GigabitEthernet1/0/1] quit # Configure Eth-Trunk 1 subinterfaces on NGFW Module_A and map them to VLANs 301, 302, and 200 respectively. NOTE In actual networking, the number of required subinterfaces depends on the number of VLANs from which packets need to be terminated. [Module_A] interface Eth-Trunk 1.301 [Module_A-Eth-Trunk1.301] vlan-type dot1q 301 [Module_A-Eth-Trunk1.301] ip address 10.1.0.1 24 [Module_A-Eth-Trunk1.301] quit [Module_A] interface Eth-Trunk 1.302 [Module_A-Eth-Trunk1.302] vlan-type dot1q 302 [Module_A-Eth-Trunk1.302] ip address 10.2.0.1 24 [Module_A-Eth-Trunk1.302] quit [Module_A] interface Eth-Trunk 1.200 [Module_A-Eth-Trunk1.200] vlan-type dot1q 200 [Module_A-Eth-Trunk1.200] ip address 10.3.0.1 24 [Module_A-Eth-Trunk1.200] quit # Add the two interfaces on the panel of NGFW Module_A to Eth-Trunk 0. [Module_A] interface Eth-Trunk 0 [Module_A-Eth-Trunk0] description hrp_interface [Module_A-Eth-Trunk0] ip address 10.10.0.1 24 [Module_A-Eth-Trunk0] quit [Module_A] interface GigabitEthernet 0/0/1 [Module_A-GigabitEthernet0/0/1] Eth-Trunk 0 [Module_A-GigabitEthernet0/0/1] quit [Module_A] interface GigabitEthernet 0/0/2 [Module_A-GigabitEthernet0/0/2] Eth-Trunk 0 [Module_A-GigabitEthernet0/0/2] quit # Assign the interfaces of NGFW Module_A to security zones. [Module_A] firewall zone untrust [Module_A-zone-untrust] add interface Eth-Trunk 1.200 [Module_A-zone-untrust] quit [Module_A] firewall zone dmz [Module_A-zone-dmz] add interface Eth-Trunk 1.302 [Module_A-zone-dmz] quit [Module_A] firewall zone trust [Module_A-zone-trust] add interface Eth-Trunk 1.301 [Module_A-zone-trust] quit [Module_A] firewall zone name hrp Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 69 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [Module_A-zone-hrp] set priority 75 [Module_A-zone-hrp] add interface Eth-Trunk 0 [Module_A-zone-hrp] quit # Configure device name on NGFW Module_B. <sysname> system-view [sysname] sysname Module_B # Add the interfaces connecting NGFW Module_B to its connected switch to EthTrunk 1. [Module_B] interface Eth-Trunk 1 [Module_B-Eth-Trunk1] description To_SWITCHB_trunk11 [Module_B-Eth-Trunk1] quit [Module_B] interface GigabitEthernet 1/0/0 [Module_B-GigabitEthernet1/0/0] Eth-Trunk 1 [Module_B-GigabitEthernet1/0/0] quit [Module_B] interface GigabitEthernet 1/0/1 [Module_B-GigabitEthernet1/0/1] Eth-Trunk 1 [Module_B-GigabitEthernet1/0/1] quit # Configure Eth-Trunk 1 subinterfaces on NGFW Module_B and map them to VLANs 301, 302, and 200 respectively. [Module_B] interface Eth-Trunk 1.301 [Module_B-Eth-Trunk1.301] vlan-type dot1q 301 [Module_B-Eth-Trunk1.301] ip address 10.1.0.2 24 [Module_B-Eth-Trunk1.301] quit [Module_B] interface Eth-Trunk 1.302 [Module_B-Eth-Trunk1.302] vlan-type dot1q 302 [Module_B-Eth-Trunk1.302] ip address 10.2.0.2 24 [Module_B-Eth-Trunk1.302] quit [Module_B] interface Eth-Trunk 1.200 [Module_B-Eth-Trunk1.200] vlan-type dot1q 200 [Module_B-Eth-Trunk1.200] ip address 10.3.0.2 24 [Module_B-Eth-Trunk1.200] quit # Add the two interfaces on the panel of NGFW Module_B to Eth-Trunk 0. [Module_B] interface Eth-Trunk 0 [Module_B-Eth-Trunk0] description hrp_interface [Module_B-Eth-Trunk0] ip address 10.10.0.2 24 [Module_B-Eth-Trunk0] quit [Module_B] interface GigabitEthernet 0/0/1 [Module_B-GigabitEthernet0/0/1] Eth-Trunk 0 [Module_B-GigabitEthernet0/0/1] quit [Module_B] interface GigabitEthernet 0/0/2 [Module_B-GigabitEthernet0/0/2] Eth-Trunk 0 [Module_B-GigabitEthernet0/0/2] quit # Assign the interfaces of NGFW Module_B to security zones. [Module_B] firewall zone untrust [Module_B-zone-untrust] add interface Eth-Trunk 1.200 [Module_B-zone-untrust] quit [Module_B] firewall zone dmz [Module_B-zone-dmz] add interface Eth-Trunk 1.302 [Module_B-zone-dmz] quit [Module_B] firewall zone trust [Module_B-zone-trust] add interface Eth-Trunk 1.301 [Module_B-zone-trust] quit [Module_B] firewall zone name hrp [Module_B-zone-hrp] set priority 75 [Module_B-zone-hrp] add interface Eth-Trunk 0 [Module_B-zone-hrp] quit Step 2 On NGFW Module, configure a default route to the Internet. # Default route from NGFW Module_A to the Internet Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 70 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [Module_A] ip route-static 0.0.0.0 0.0.0.0 10.3.0.5 # Default route from NGFW Module_B to the Internet [Module_B] ip route-static 0.0.0.0 0.0.0.0 10.3.0.5 Step 3 Configure hot standby on NGFW Modules. # Configure VRRP groups on NGFW Module_A. [Module_A] interface Eth-Trunk 1.301 [Module_A-Eth-Trunk1.301] vrrp vrid 1 virtual-ip 10.1.0.3 active [Module_A-Eth-Trunk1.301] quit [Module_A] interface Eth-Trunk 1.302 [Module_A-Eth-Trunk1.302] vrrp vrid 2 virtual-ip 10.2.0.3 active [Module_A-Eth-Trunk1.302] quit [Module_A] interface Eth-Trunk 1.200 [Module_A-Eth-Trunk1.200] vrrp vrid 3 virtual-ip 10.3.0.3 active [Module_A-Eth-Trunk1.200] quit # Specify the heartbeat interface and enable hot standby on NGFW Module_A. [Module_A] hrp interface Eth-Trunk 0 [Module_A] hrp enable # Configure VRRP groups on NGFW Module_B. [Module_B] interface Eth-Trunk 1.301 [Module_B-Eth-Trunk1.301] vrrp vrid 1 virtual-ip 10.1.0.3 standby [Module_B-Eth-Trunk1.301] quit [Module_B] interface Eth-Trunk 1.302 [Module_B-Eth-Trunk1.302] vrrp vrid 2 virtual-ip 10.2.0.3 standby [Module_B-Eth-Trunk1.302] quit [Module_B] interface Eth-Trunk 1.200 [Module_B-Eth-Trunk1.200] vrrp vrid 3 virtual-ip 10.3.0.3 standby [Module_B-Eth-Trunk1.200] quit # Specify the heartbeat interface and enable hot standby on NGFW Module_B. [Module_B] hrp interface Eth-Trunk 0 [Module_B] hrp enable [Module_B] hrp standby-device //This command is required only in versions earlier than V100R001C30SPC300. NOTE After hot standby is configured, the configurations and sessions on the active device are synchronized to the standby device; therefore, you only need to perform the following configurations on the active NGFW Module_A. Before configuring intrusion prevention, ensure that the required license is loaded and the intrusion prevention signature database is the latest version. When configuring intrusion prevention, use the default intrusion prevention profile default. Step 4 Configure security services on NGFW Modules. # On NGFW Module_A, configure a security policy to allow intranet users to access the server zone (network segment 10.2.0.0/24). HRP_A[Module_A] security-policy HRP_A[Module_A-policy-security] rule name policy_to_server HRP_A[Module_A-policy-security-rule-policy_to_server] source-zone trust HRP_A[Module_A-policy-security-rule-policy_to_server] destination-zone dmz HRP_A[Module_A-policy-security-rule-policy_to_server] destination-address 10.2.0.0 24 HRP_A[Module_A-policy-security-rule-policy_to_server] service http ftp HRP_A[Module_A-policy-security-rule-policy_to_server] action permit HRP_A[Module_A-policy-security-rule-policy_to_server] quit HRP_A[Module_A-policy-security] quit Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 71 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples # On NGFW Module_A, configure a security policy to allow intranet users to access the Internet and configure intrusion prevention. HRP_A[Module_A] security-policy HRP_A[Module_A-policy-security] rule name policy_to_wan HRP_A[Module_A-policy-security-rule-policy_to_wan] source-zone trust HRP_A[Module_A-policy-security-rule-policy_to_wan] destination-zone untrust HRP_A[Module_A-policy-security-rule-policy_to_wan] source-address 10.1.0.0 24 HRP_A[Module_A-policy-security-rule-policy_to_wan] service http ftp HRP_A[Module_A-policy-security-rule-policy_to_wan] profile ips default HRP_A[Module_A-policy-security-rule-policy_to_wan] action permit HRP_A[Module_A-policy-security-rule-policy_to_wan] quit HRP_A[Module_A-policy-security] quit # Configure ASPF on NGFW Module_A. FTP is used as an example. HRP_A[Module_A] firewall interzone trust dmz HRP_A[Module_A-interzone-trust-dmz] detect ftp HRP_A[Module_A-interzone-trust-dmz] quit HRP_A[Module_A] firewall interzone trust untrust HRP_A[Module_A-interzone-trust-untrust] detect ftp HRP_A[Module_A-interzone-trust-untrust] quit # Save configurations on NGFW Module_A and NGFW Module_B. HRP_A<Module_A> save The current configurations will be written to the device. Are you sure?[Y/N] y Now saving the current configuration to the device...... Info:The Current Configuration was saved to the device successfully HRP_S<Module_B> save The current configurations will be written to the device. Are you sure?[Y/N] y Now saving the current configuration to the device...... Info:The Current Configuration was saved to the device successfully Step 5 Configure the core switches to form a CSS. 1. Install the hardware and connect the cables. For details, see the CSS Installation Guide. 2. Set the CSS connection mode (such as the CSS card connection mode), CSS ID, and CSS priority. # Configure the CSS on SwitchA. In the example, the CSS connection mode is CSS card connection mode, the CSS ID is 1, and the CSS priority is 100. <Huawei> system-view [Huawei] sysname SwitchA [SwitchA] set css mode css-card card connection mode. [SwitchA] set css id 1 [SwitchA] set css priority 100 //Set the CSS connection mode. The default mode is CSS //Set the CSS ID. The default value is 1. //Set the CSS priority. The default value is 1. # Configure the CSS on SwitchB. In the example, the CSS connection mode is CSS card connection mode, the CSS ID is 2, and the CSS priority is 10. <Huawei> system-view [Huawei] sysname SwitchB [SwitchB] set css mode css-card [SwitchB] set css id 2 [SwitchB] set css priority 10 3. Enable the CSS function. # To use SwitchA as the active switch, enable CSS on SwitchA and then restart SwitchA. Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 72 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples [SwitchA] css enable Warning: The CSS configuration will take effect only after the system is rebooted. T he next CSS mode is CSS card. Reboot now? [Y/N]:y # Enable CSS on SwitchB and then restart SwitchB. [SwitchB] css enable Warning: The CSS configuration will take effect only after the system is rebooted. T he next CSS mode is CSS card. Reboot now? [Y/N]:y 4. Check whether the CSS is established. # Log in to the CSS from the console port of any MPU and run the following command to view the CSS status. <SwitchA> display css status CSS Enable switch On Chassis Id CSS Enable CSS Status CSS Mode Priority Master Force -----------------------------------------------------------------------------Off 1 On Master CSS card 100 2 On Standby CSS card 10 Off If the CSS IDs, CSS priorities, CSS enabling status, and CSS status of the two member switches are displayed, as shown in the preceding information, the CSS has been established. You are advised to configure MAD to minimize the impact of a CSS split on services. Detailed configurations will not be described here. 5. Rename the cluster system to CSS. <SwitchA> system-view [SwitchA] sysname CSS [CSS] Step 6 Configure switch interfaces. 1. Create VLANs. [CSS] vlan batch 200 301 to 302 2. Add the switch interfaces connected to NGFW Module_A to Eth-Trunk 10. [CSS] interface eth-trunk 10 [CSS-Eth-Trunk10] description To_Module_A [CSS-Eth-Trunk10] port link-type trunk [CSS-Eth-Trunk10] trunkport xgigabitethernet 1/1/0/0 to 1/1/0/1 [CSS-Eth-Trunk10] undo port trunk allow-pass vlan 1 [CSS-Eth-Trunk10] port trunk allow-pass vlan 200 301 to 302 //Direct traffic from different VLANs to the NGFW Module. [CSS-Eth-Trunk10] quit 3. Add the switch interfaces connected to NGFW Module_B to Eth-Trunk 11. [CSS] interface eth-trunk 11 [CSS-Eth-Trunk11] description To_Module_B [CSS-Eth-Trunk11] port link-type trunk [CSS-Eth-Trunk11] trunkport xgigabitethernet 2/1/0/0 to 2/1/0/1 [CSS-Eth-Trunk11] undo port trunk allow-pass vlan 1 [CSS-Eth-Trunk11] port trunk allow-pass vlan 200 301 to 302 //Direct traffic from different VLANs to the NGFW Module. [CSS-Eth-Trunk11] quit 4. Configure Eth-Trunk 2 connected to intranet users. Adding the interfaces to Eth-Trunk 2 is not mentioned here. [CSS] interface eth-trunk 2 [CSS-Eth-Trunk2] port link-type trunk [CSS-Eth-Trunk2] undo port trunk allow-pass vlan 1 [CSS-Eth-Trunk2] port trunk allow-pass vlan 301 [CSS-Eth-Trunk2] quit Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 73 Sx300 Series Switches Typical Configuration Examples 5. 2 Comprehensive Configuration Examples Configure Eth-Trunk 3 connected to intranet users. Adding the interfaces to Eth-Trunk 3 is not mentioned here. [CSS] interface eth-trunk 3 [CSS-Eth-Trunk3] port link-type trunk [CSS-Eth-Trunk3] undo port trunk allow-pass vlan 1 [CSS-Eth-Trunk3] port trunk allow-pass vlan 302 [CSS-Eth-Trunk3] quit 6. Configure Eth-Trunk 5 connected to the egress router. Adding the interfaces to Eth-Trunk 5 is not mentioned here. [CSS] interface eth-trunk 5 [CSS-Eth-Trunk5] port link-type access [CSS-Eth-Trunk5] port default vlan 200 [CSS-Eth-Trunk5] quit Step 7 Configure upstream and downstream devices. 1. Configure the upstream interface Eth-Trunk 2 on the intranet switch to work in trunk mode and allow traffic from VLAN 301 to pass. 2. Configure the upstream interface Eth-Trunk 3 on the server switch to work in trunk mode and allow traffic from VLAN 302 to pass. 3. Set the gateway address of intranet PCs to the virtual IP address (10.1.0.3) of the VRRP group to which Eth-Trunk 1.301 belongs. 4. Set the gateway address of servers to the virtual IP address (10.2.0.3) of the VRRP group to which Eth-Trunk 1.302 belongs. 5. The next-hop address of the route from the egress router to the intranet is the virtual IP address (10.3.0.3) of the VRRP group to which Eth-Trunk 1.200 belongs. ----End Verification 1. Run the display hrp state command on NGFW Module_A to check the current HRP status. If the following output is displayed, an HRP relationship is successfully established. HRP_A[Module_A] display hrp state The firewall's config state is: ACTIVE Backup channel usage: 0.01% Time elapsed after the last switchover: 0 days, 0 hours, 1 minutes Current state of virtual routers configured as active: Eth-Trunk1.200 vrid 3 : active (GigabitEthernet1/0/0) : up (GigabitEthernet1/0/1) : up Eth-Trunk1.302 vrid 2 : active (GigabitEthernet1/0/0) : up (GigabitEthernet1/0/1) : up Eth-Trunk1.301 vrid 1 : active (GigabitEthernet1/0/0) : up (GigabitEthernet1/0/1) : up 2. Check whether the access from the intranet to the Internet succeeds and check the session table of each NGFW Module. HRP_A[Module_A] display firewall session table Current Total Sessions : 1 http VPN: public --> public 10.1.0.10:22048 --> 3.3.3.3:80 HRP_S[Module_B] display firewall session table Current Total Sessions : 1 http VPN: public --> public Remote 10.1.0.10:22048 --> 3.3.3.3:80 Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 74 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples According to the preceding output, NGFW Module_A has created a session entry for the access from the intranet to the Internet. A session entry with the Remote tag exists on NGFW Module_B, which indicates that session backup succeeds after you configure hot standby. 3. Check whether the access from users in the intranet to servers succeeds and check the session table of each NGFW Module. HRP_A[Module_A] display firewall session table Current Total Sessions : 1 http VPN: public --> public 10.1.0.10:22048 --> 10.2.0.8:80 HRP_S[Module_A] display firewall session table Current Total Sessions : 1 http VPN: public --> public Remote 10.1.0.10:22048 --> 10.2.0.8:80 4. Configure a PC in the Trust zone to constantly ping the public address and run the shutdown command on Eth-trunk1 of NGFW Module_A. Then check the status switchover of the NGFW Module and discarded ping packets. If the status switchover is normal, NGFW Module_B becomes the active device and carries services. The command prompt of NGFW Module_B is changed from HRP_S to HRP_A, and the command prompt of NGFW Module_A is changed from HRP_A to HRP_S. No or several ping packets (1 to 3 packets, depending on actual network environments) are discarded. Run the undo shutdown command on Eth-trunk1 of NGFW Module_A and check the status switchover of the NGFW Module and discarded ping packets. If the status switchover is normal, NGFW Module_A becomes the active device and starts to carry service after the preemption delay (60s by default) expires. The command prompt of NGFW Module_A is changed from HRP_S to HRP_A, and the command prompt of NGFW Module_B is changed from HRP_A to HRP_S. No or several ping packets (1 to 3 packets, depending on actual network environments) are discarded. Configuration Scripts Configuration scripts of the NGFW Modules: Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 75 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples NGFW Module_A NGFW Module_B # sysname Module_A # hrp enable hrp interface Eth-Trunk0 # interface Eth-Trunk0 description hrp_interface ip address 10.10.0.1 255.255.255.0 # interface Eth-Trunk1 description To_SWITCHA_trunk10 # interface Eth-Trunk1.200 vlan-type dot1q 200 ip address 10.3.0.1 255.255.255.0 vrrp vrid 3 virtual-ip 10.3.0.3 active # interface Eth-Trunk1.301 vlan-type dot1q 301 ip address 10.1.0.1 255.255.255.0 vrrp vrid 1 virtual-ip 10.1.0.3 active # interface Eth-Trunk1.302 vlan-type dot1q 302 ip address 10.2.0.1 255.255.255.0 vrrp vrid 2 virtual-ip 10.2.0.3 active # interface GigabitEthernet0/0/1 eth-trunk 0 # interface GigabitEthernet0/0/2 eth-trunk 0 # interface GigabitEthernet1/0/0 eth-trunk 1 # interface GigabitEthernet1/0/1 eth-trunk 1 # firewall zone trust set priority 85 add interface Eth-Trunk1.301 # firewall zone untrust set priority 5 add interface Eth-Trunk1.200 # firewall zone dmz set priority 50 add interface Eth-Trunk1.302 # firewall zone name hrp set priority 75 add interface Eth-Trunk0 # firewall interzone trust untrust detect ftp # firewall interzone trust dmz detect ftp # ip route-static 0.0.0.0 0.0.0.0 10.3.0.5 # security-policy rule name policy_to_server # sysname Module_B # hrp enable hrp interface Eth-Trunk0 hrp standby-device //This command is required only in versions earlier than V100R001C30SPC300. # interface Eth-Trunk0 description hrp_interface ip address 10.10.0.2 255.255.255.0 # interface Eth-Trunk1 description To_SWITCHB_trunk11 # interface Eth-Trunk1.200 vlan-type dot1q 200 ip address 10.3.0.2 255.255.255.0 vrrp vrid 3 virtual-ip 10.3.0.3 standby # interface Eth-Trunk1.301 vlan-type dot1q 301 ip address 10.1.0.2 255.255.255.0 vrrp vrid 1 virtual-ip 10.1.0.3 standby # interface Eth-Trunk1.302 vlan-type dot1q 302 ip address 10.2.0.2 255.255.255.0 vrrp vrid 2 virtual-ip 10.2.0.3 standby # interface GigabitEthernet0/0/1 eth-trunk 0 # interface GigabitEthernet0/0/2 eth-trunk 0 # interface GigabitEthernet1/0/0 eth-trunk 1 # interface GigabitEthernet1/0/1 eth-trunk 1 # firewall zone trust set priority 85 add interface Eth-Trunk1.301 # firewall zone untrust set priority 5 add Eth-Trunk1.200 # firewall zone dmz set priority 50 add interface Eth-Trunk1.302 # firewall zone name hrp set priority 75 add interface Eth-Trunk0 # firewall interzone trust untrust detect ftp # firewall interzone trust dmz detect ftp # ip route-static 0.0.0.0 0.0.0.0 10.3.0.5 # Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 76 Sx300 Series Switches Typical Configuration Examples 2 Comprehensive Configuration Examples NGFW Module_A NGFW Module_B source-zone trust destination-zone dmz destination-address 10.2.0.0 mask 255.255.255.0 service http service ftp action permit rule name policy_to_wan source-zone trust destination-zone untrust source-address 10.1.0.0 mask 255.255.255.0 service http service ftp profile ips default action permit # return security-policy rule name policy_to_server source-zone trust destination-zone dmz destination-address 10.2.0.0 mask 255.255.255.0 service http service ftp action permit rule name policy_to_wan source-zone trust destination-zone untrust source-address 10.1.0.0 mask 255.255.255.0 service http service ftp profile ips default action permit # return Configuration script of CSS: # ----CSS configuration---vlan batch 200 301 to 302 # interface Eth-Trunk2 port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 301 # interface Eth-Trunk3 port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 302 # interface Eth-Trunk5 port link-type access port default vlan 200 # interface Eth-Trunk10 description To_Module_A port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 200 301 to 302 # interface Eth-Trunk11 description To_Module_B port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 200 301 to 302 # interface XGigabitEthernet1/1/0/0 eth-Trunk 10 # interface XGigabitEthernet1/1/0/1 eth-Trunk 10 # interface XGigabitEthernet2/1/0/0 eth-Trunk 11 # interface XGigabitEthernet2/1/0/1 eth-Trunk 11 # return Issue 34 (2022-10-26) Copyright © Huawei Technologies Co., Ltd. 77
Anuncio
Documentos relacionados
Descargar
Anuncio
Añadir este documento a la recogida (s)
Puede agregar este documento a su colección de estudio (s)
Iniciar sesión Disponible sólo para usuarios autorizadosAñadir a este documento guardado
Puede agregar este documento a su lista guardada
Iniciar sesión Disponible sólo para usuarios autorizados