The SCADA That Didn`t Cry Wolf
Anuncio

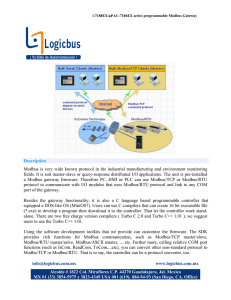
The SCADA That Didn’t Cry Wolf: Who’s Really Attacking Your SCADA Devices Kyle Wilhoit Sr. Threat Researcher Trend Micro 1 Glossary HMI: Human Machine Interface IED: Intelligent Electronic Device SCADA: Supervisory Control And Data Acquisition RTU: Remote Terminal Unit Historian: Data Historian Modbus: Common ICS Protocol DNP3: Common ICS Protocol 10/31/13 Confidential | Copyright 2012 Trend Micro Inc. 2 Typical ICS Deployment 10/31/13 Confidential | Copyright 2012 Trend Micro Inc. 3 Modbus • Oldest ICS Protocol • Controls I/O Interfaces (MOSTLY!!!!) • No authentication or encryption! (Surprise!!!) • No broadcast suppression • Vulnerabilities are published 10/31/13 Confidential | Copyright 2012 Trend Micro Inc. 4 Security Concerns- ICS vs. IT ICS • Correct commands issued (Integrity) • Limit interruptions (Availability) • Protect the data (Confidentiality) 10/31/13 Confidential | Copyright 2012 Trend Micro Inc. 5 IT • Protect the data (Confidentiality) • Correct commands issued (Integrity) • Limit interruptions (Availability) Primary Security Concerns • HMI: Allows arbitrary command execution as well as set point modifications. • Data Historian: Allows inbound traffic to secure network segments. (Replication of data) • RTU: Allows remote communication ability And many more… Incidents Exist • First half of 2013 • Over 200 confirmed “incidents” SCADA Internet Facing • • • • • Google-fu Shodan ERIPP Pastebin Twitter SCADA Internet Facing Story Time! • All Internet facing… • No security measures in place Attacks • Attacked several times- over a period of months • Attackers gained access • Exfiltrated data • Not made public • This is not a story… • This happened… Story Time! In my basement… Enter Honeypots… • • • • 12 total honeypots 8 different countries Running since Jan, 2013 Combination of *nix, Windows, and Nov. 2012-March 2013 embedded systems Phase 1: Physical Deployment • Small town in rural America • Water pump controlling water pressure/ availability • Population 18,000~ 10/31/13 Confidential | Copyright 2012 Trend Micro Inc. 15 Physical Deployment • Fake water pressure system Internet facing • Very little security measures in place • Could cause catastrophic water pressure failures if compromised 10/31/13 Confidential | Copyright 2012 Trend Micro Inc. 16 What They See 10/31/13 Confidential | Copyright 2012 Trend Micro Inc. 17 Physical Deployment 10/31/13 Confidential | Copyright 2012 Trend Micro Inc. 18 Attack Profile- Country of Origin 2% 2% 2% 2% 2% 2% US 19% 6% LAOS UK 4% 2% 2% 12% CHINA NETHERLANDS 8% JAPAN BRAZIL 35% POLAND 10/31/13 Confidential | Copyright 2012 Trend Micro Inc. 19 • • • • 12 total honeypots 8 different countries Running since Jan, 2013 Combination of *nix, Windows, and March. 2013-July 2013 embedded systems Phase 2: Virtualized Environment • Water pump controlling water pressure/ availability • Population combined ~50 million Logically… 10/31/13 Confidential | Copyright 2012 Trend Micro Inc. 22 Architecture Some Tools Used Modbus.py OpenDNP3 PiFace Vulnerabilities Presented “If you can ping it, you own it” • SNMP vulns (read/write SNMP, packet sniffing, IP spoofing) • Specific ICS Vendor vulnerabilities • HMI (Server) Vulnerabilities • Authentication limitations • Limits of Modbus/DNP3 authentication/encryption • VxWorks Vulnerability (FTP) • Open access for certain ICS modifications- fan speed, temperature, and utilization. What’s an Attack? • ONLY attacks that were targeted • ONLY attempted modification of pump system (FTP, Telnet, Modbus, set points, etc.) • ONLY attempted modification via Modbus/DNP3 • DoS/DDoS will be considered attacks Total Attacks -74 attacks Non-Critical Attack ProfileSource Countries -63 non-critical attacks Critical Attack Profile- Source Countries -11 critical attacks Some Attack Stats Data exfiltration attempt Modification of CPU fan speed Modbus traffic modification HMI access Modify pump pressure Modify temperature output Shutdown pump system 0 0.5 1 1.5 2 2.5 3 3.5 Spear Phished TO: CITYWORKS@<HOSTNAME OF OUR CITY>.COM “ Hello sir, I am <name of city administrator> and would like the attached statistics filled out and sent back to me. Kindly Send me the doc and also advise if you have questions. Look forward you hear from you soon ....Mr. <city administrator name> ” Cityrequest.doc • Decoy doc- not much substance Cityrequest.doc Dropped Files • CityRequest.doc • File gh.exe dumps all local password hashes – <gh.exe –w> • File ai.exe shovels a shell back to a dump server. – < ai.exe –d1 (Domain) –c1 (Compare IP) –s (Service) > • Malware communicating to a drop/CnC server in China. • exploiting CVE 2012-0158 • Malware communicating to a drop/CnC server in USA – 70.254.245.X – 70.254.245.X – Has been taken down…by the US government Execution • Upon execution of CityRequest.docx, files leaving the server in question after 5 days. – Fake VPN config file – Network statistics dump – SAM database dump – Gain persistence via process migration • Won’t execute on Office 2010. Exfiltration: Days 1-4 Exfiltration: Days 5-17 APT1 Report • APT1 (Comment Crew) report released in Feb 2013. • Included many APT variants we’ve seen. • One of particular interest was HACKSFASE. • Commonly used in energy sector. Examination Attribution 10/31/13 Confidential | Copyright 2012 Trend Micro Inc. 40 Attribution • IP • BeEF • Code Analysis BeEF Usage • • • • • Detect Tor Get Registry Keys Get_Physical_Location Get_System_Info Get_Internal_IP Attacker Profile • Most attacks appeared to be non-targeted • Many attackers were “opportunists” • Some were targeted… Some Takeaways • • • • Red team/Blue team often Perform specialized vulnerability assessments Control contractors Perform basic security controls • Network segmentation • Two-factor authentication • Patch your stuff! • Lockdown external media • Manage vulnerabilities • Classify your data/assets • etc. Shout Email: [email protected] Non-Work: [email protected] Twitter @lowcalspam